SnoopSnitch for Android warns you about fake base stations
So-called IMSI-Catchers and StingRays act as false mobile towers that sit between mobile devices such as smartphones and real towers by mobile providers.
These fake towers can intercept mobile phone traffic and track movement of the individuals carrying the phone, and even manipulate the device remotely.
SnoopSnitch is a brand new application for Android devices that provides phone owners with information about potential threats in their vicinity.
Note: The application requires root access. It furthermore will only run on Android 4.1 or later operating systems and requires a Qualcomm chipset. The app has been tested successfully on a handful devices already including the Moto E and G, Sony Xperia Z1, LG G2, Samsung S3 Neo and Samsung S4. Other devices like the Nexus 5 or Samsung Galaxy S3 are not supported right now.
You can download the app from Google Play or directly from the project website. There is also an option to get the source code and compile the app in a local development environment.
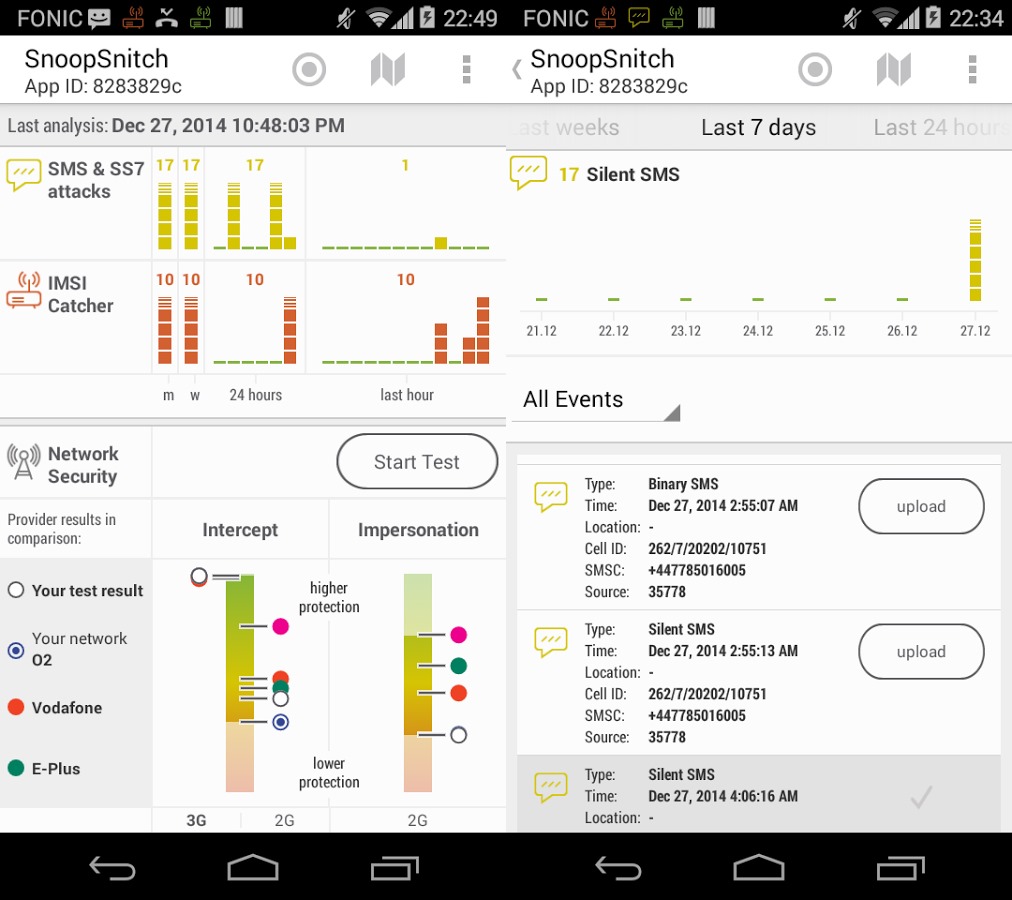
The app "collects and analyzes mobile radio data" while it is running to warn you about potential threats such as fake base stations, user tracking and over-the-air updates.
Once you have installed the app you can run tests to identify threats. Tests include placing an outgoing call to a number that is always busy and sending a SMS message to an invalid number.
The creators of the app note that service charges may apply even though it is unlikely in the majority of cases. They still advise to use a pre-paid SIM card for the test as it provides better options to control these charges.
Users of the application can upload test results to a remote server. The data uploaded by all users to the server is made available to all users of the application. This means that users can access all security events and suspicious activity provided that these have been uploaded to the server previously.
A related application is IMSI Catcher Detector which concentrates on fake base stations only though.
Closing Words
I can see this being used in business environments and other sensitive areas to make sure that traffic is not flowing through fake base stations.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments