How to prevent HSTS tracking in Firefox
HTTP Strict Transport Security (HSTS) was designed to help secure websites (those using HTTPS) by declaring to web browsers that they should communicate only via HTTPS with the server to protect connections against downgrade attacks and cookie hijacking.
Mozilla implemented support for HSTS in its current form in Firefox in 2014 and it has been active in all Firefox versions ever since.
Ars Technica were among the first to raise concerns about the implementation of HSTS in web browsers as it allowed site operators to plant supercookies in browsers using the technology that was designed to improve user security.
A demo site was created by Sam Greenhalgh to demonstrate the concept. When you visit the site in a browser supporting HSTS, you are assigned a unique ID which persists across browser sessions and can be used to track you because of it.
![]()
Note: This issue is not limited to the Firefox web browser as Google Chrome and other browsers who have implemented the feature are vulnerable to HSTS tracking as well.
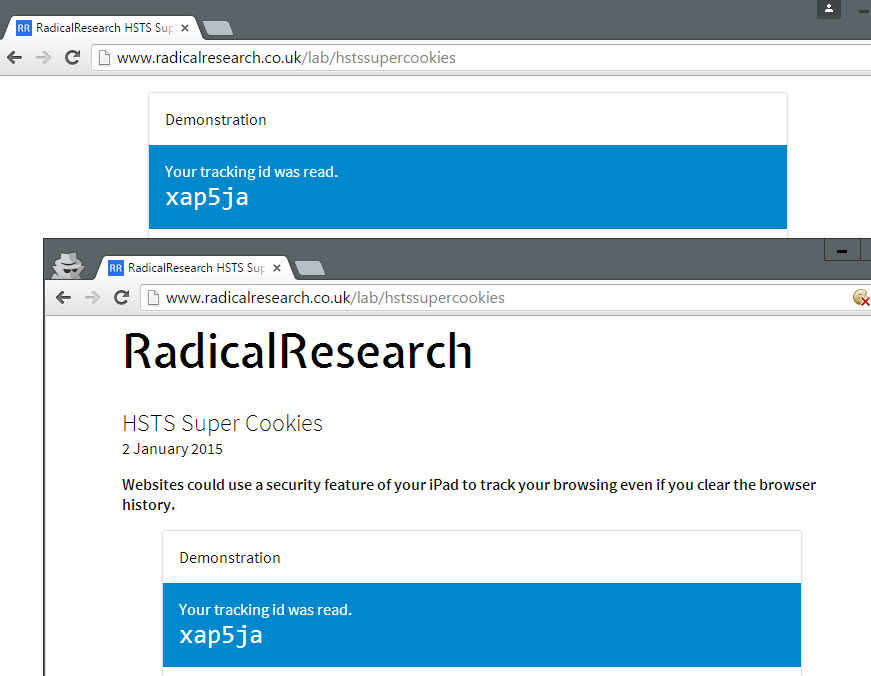
How HSTS is handled by Firefox currently
Firefox saves HSTS information to the file SiteSecurityServiceState.txt which you find in the root of your Firefox profile folder.
The easiest way to open it is to load about:support in Firefox's address bar and to click on the "show folder" button on the page after it has loaded. This opens the profile folder of Firefox in the default system file browser.
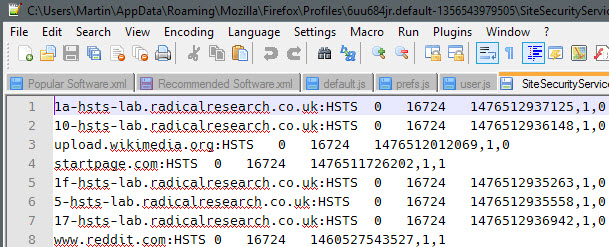
When you open the file in a plain text editor you will get a list of domain names and values associated with them including an expiration date.
Firefox handles HSTS in private browsing mode and regular browsing mode differently.
- Regular browsing mode: HSTS persists across sessions.
- Private browsing mode: HSTS information are deleted after the session.
Note that sites can access HSTS information created during regular browsing sessions when you enter private browsing mode in that session.
Protection against HSTS tracking
Unlike cookies, HSTS offers no whitelist or blacklist approach. The feature is enabled by default and there appears to be no preference to disable it.
Even if there would be an option to do so, it would affect security while browsing the Internet.
1. Only use Private Browsing Mode
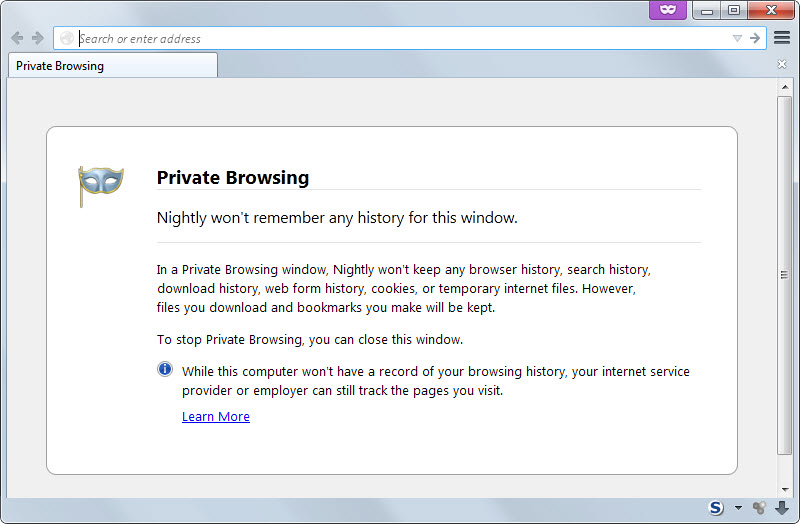
Since Firefox is clearing HSTS information after you close private browsing sessions, it is currently the best option to prevent supercookie tracking without compromising security.
To launch Firefox in private browsing mode, use the shortcut Ctrl-Shift-P, or hit the Alt-key and select File > New Private Window.
2. Clear the Site Preferences on exit
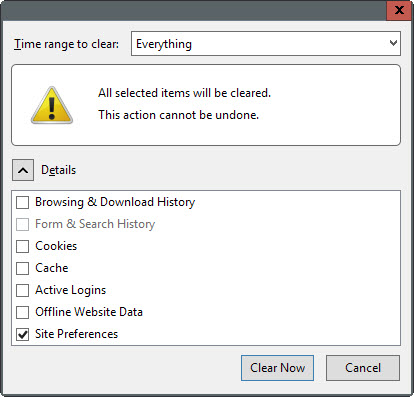
The second option that you have is to clear Site Preferences whenever you close the Firefox browser. This gets rid of all HSTS information saved to the SiteSecurityServiceState.txt file but impacts other site specific preferences such as site-specific permissions or zoom levels as they get cleared as well by the operation.
Note: This works in Google Chrome as well. Tap on Ctrl-Shift-Del to open the clear browsing data dialog in the browser. Make sure "cookies and other site and plugin data" is selected and hit clear browsing data afterwards.
This will remove cookies and site preferences as well.
3. Remove entries from the HSTS file manually
The HSTS file is a plain text document which means that you can manipulate data in it easily using text editors.
Make sure Firefox is closed before you do so as content will be overwritten when Firefox is terminated.
The method gives you full control over HSTS but it requires manual intervention regularly, and may not be suitable because of this.
One option that you may have is to keep select sites in and make the file read-only afterwards to block new entries to it.
You will still need to edit it manually regularly as HSTS information have an expiry date.
4. Remove HSTS file data automatically
Programs like CCleaner support the cleaning of HSTS Supercookies but you can also run a local command such as echo ' ' >/SiteSecurityServiceState.txt on the file regularly to remove it. If you add it to a batch file and run it on system start or shut down, then you should not have to worry about HSTS information persisting across sessions.
5. Make the HSTS file read-only
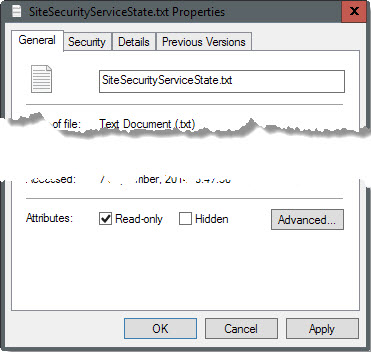
This radical approach blocks Firefox from saving information to the HSTS file. While that is effective in preventing tracking, it means that the browser cannot make use of HSTS to improve security.
To make it read-only on Windows, right-click the file and select properties from the context menu. Locate the read-only box on the properties page and check it. Click ok afterwards to apply the change.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments