Are you identifiable by extensions, logins and your browser?
Are you identifiable is a new web service that answers whether Internet sites may identify you based on your extensions, logins, and web browser.
Online privacy is a hot topic, and making sure that you you are not tracked or traced online may soon require a master's degree in privacy.
New technologies, the rise of HTML5 and all that came with it for instance, added new capabilities. As is the case with these things usually, they can be used for good and bad.
It is no longer enough to use a VPN, or a content blocker to keep some of your privacy while you are on the Internet. You also need to know and deal with new technologies such as WebRTC or intermediate CA caching, to avoid leaks or browser fingerprinting scripts.
Are you identifiable
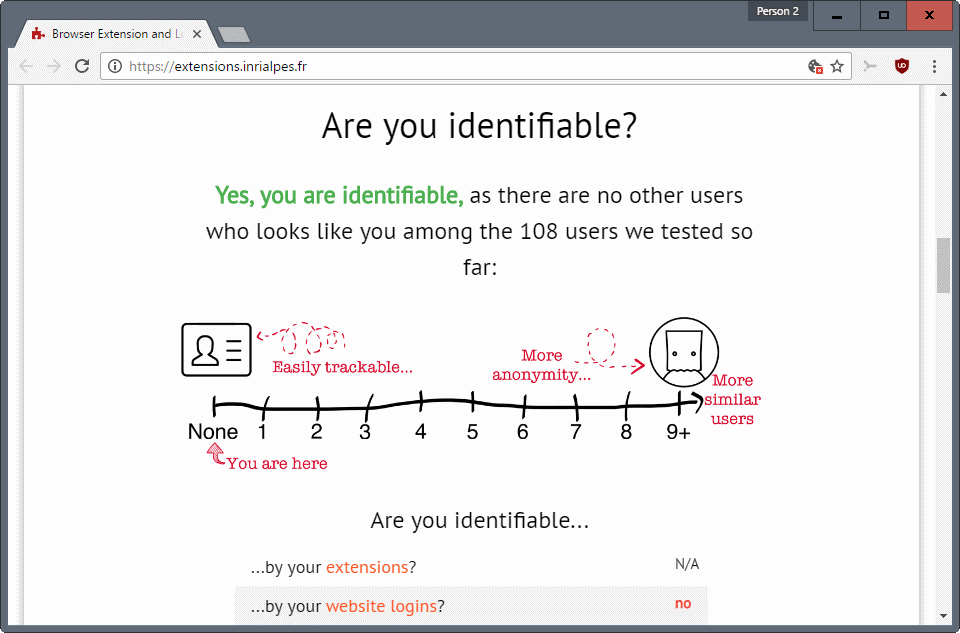
Are you identifiable looks like any other browser fingerprinting site on first glance. Load the site, click on the I agree button to start the scan, and the results are displayed to you after a couple of seconds.
What is different about it is that it does not just check information the browser reveals to the site, e.g. the window resolution, browser version, or language, but tries to gather information on extensions and website logins as well.
The extension detection works by trying to detect resources, such as icons, that extensions use. All the site does is therefore check whether resources exist. If they do, it knows that there is a high probability that the extension is installed.
The developers of the browser extension and login-leak experiment have collected resources of about 12,000 Google Chrome extensions.
While that is a pretty large number, it means that the part of the test is limited to Google Chrome right now. It may work on other Chromium-based browsers as well, as they may use the same resources if the extensions are installed in those browsers.
The login detection runs a test to see if you are signed in to various popular online properties such as Facebook or Twitter. It uses image embeds for that, and tests these images to see whether the image is loaded or not. This allows the service to determine whether you are signed in to the service in question, or not.
Another method that it uses abuses Content-Security Policy by using the feature to determine whether contents get loaded, or not.
A technical explanation of all three methods is provided on the how page on the service's site.
The browser fingerprinting part on the other hand retrieves information from the browser just like other tests of its kind do.
Closing Words
One of the downsides of the test is that it just started. It has a very low sample size right now so that uniqueness may come from that more than it comes from what the site's scripts detect while it is running.
Still, the interesting part is that it merges these different methods into a single test. It determines uniqueness or the ability to track users for each test individually, but also for all three tests combined.
Now You: Are you identifiable according to the site?
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments