Microsoft, LastPass and others post solutions to handle Superfish
An adware called Superfish is making big waves currently on the Internet after news spread that PC manufacturer Lenovo shipped some -- it is still not clear which devices are affected -- consumer PC models with the software preinstalled.
The core purpose of Superfish is to display advertisement to users based on what they are looking at in web browsers. It injects advertisement on web pages that users visit in browsers.
While that is bad enough, it is only part of the reason why Superfish is universally condemned currently. What is even more problematic than that is that the program installs a root certificate on the system. This is done by the software to gain access to https traffic as well, something which it would not otherwise be capable of.
The certificate was cracked recently which means that attackers can exploit it for man in the middle attacks.
Lenovo posted Superfish removal instructions yesterday but it is not the only company that sprang into action after the news broke.
Microsoft for instance updated Windows Defender, the built-in Windows security program to detect the Superfish certificate and VisualDiscovery program so that affected users can remove it from their systems using it.
Filippo Valsorda posted a screenshot of Windows Defender detecting Superfish on Twitter today.
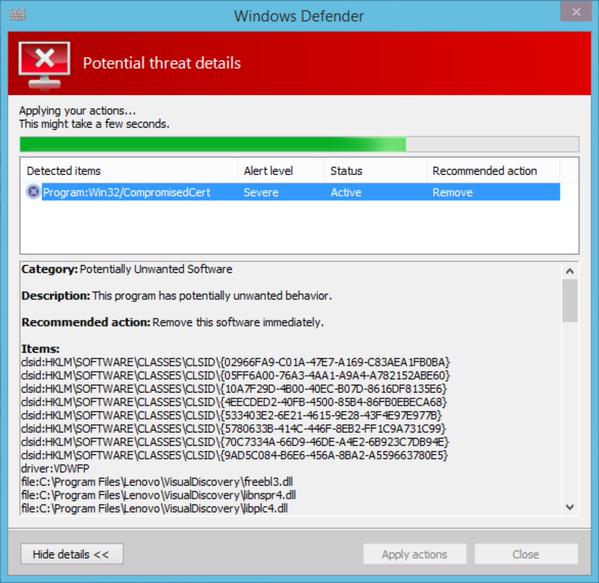
Microsoft has not confirmed the integration yet but an update to the program's definition file was released today by the company.
You can check for the update manually in Windows Defender or download the most recent definition files from this page on the Microsoft website.
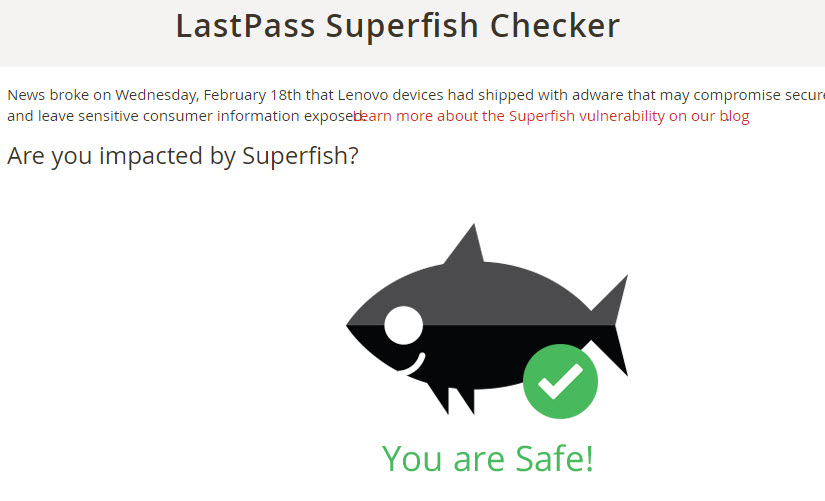
LastPass, makers of the popular password manager of the same name, have published Superfish Checker, a page on their website which detects whether Superfish is installed on the computer you are accessing the page with.
Besides checking whether you are affected or not by it, it lists removal instructions for the program and certificate.
The company is not the only one that published an online check tool. You can also use the Superfish CA test instead which tells you if the certificate is installed on your system. It recommends to perform the check with all browsers installed on the system.
If you are affected, you may also want to check out the removal instructions on the EFF website which offers a detailed guide to remove the Superfish software and certificate.
The whole Superfish incident turned quickly into a PR disaster for Lenovo. While the issue was first reported on tech sites (well actually first on the Lenovo forum some time ago) it was quickly picked up by newspapers worldwide.
If you search for Superfish right now you find articles about it on Forbes, The Independent, The Wallstreet Journal, Der Spiegel, the BBC and dozens if not hundreds more.
Update: Lenovo has published a list of affected products (stating that they may be affected):
- E-Series: E10-30
- Flex-Series:Flex2 14, Flex2 15, Flex2 14D, Flex2 15D, Flex2 14 (BTM), Flex2 15 (BTM), Flex 10
- G-Series: G410, G510, G40-70, G40-30, G40-45, G50-70, G50-30, G50-45
- M-Series: Miix2 – 8, Miix2 – 10, Miix2 – 11,
- S-Series: S310, S410, S415; S415 Touch, S20-30, S20-30 Touch, S40-70
- U-Series: U330P, U430P, U330Touch, U430Touch, U540Touch
- Y-Series: Y430P, Y40-70, Y50-70
- Yoga-Series: Yoga2-11BTM, Yoga2-11HSW, Yoga2-13, Yoga2Pro-13
- Z-Series: Z40-70, Z40-75, Z50-70, Z50-75
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments