Check if Windows is affected by the Freak Attack vulnerability
Freak Attack is the name of a new SSL/TLS vulnerability that came to light on March 3, 2015. The vulnerability can be exploited by hackers to weaken the encryption used between clients and servers when HTTPs connections are used.
Affected are servers, according to a site that is tracking the issue 9.5% of Alexa's top 1 million domain names but also web browsers such as Chrome, Safari and Internet Explorer.
Browser's are not necessarily vulnerable on all systems they support. Chrome is for instance vulnerable on Android and Mac OS X but not on Windows.
Firefox appears to be the only browser not affected by the vulnerability at all on all systems it supports.
Since Internet Explorer is affected by the vulnerability on Windows, it is important to check whether your PC is vulnerable and do something about it if that is the case.
The easiest way to do that is to use the Freak Client Test Tool which tests for the vulnerability and reports back if your browser is vulnerable or not.
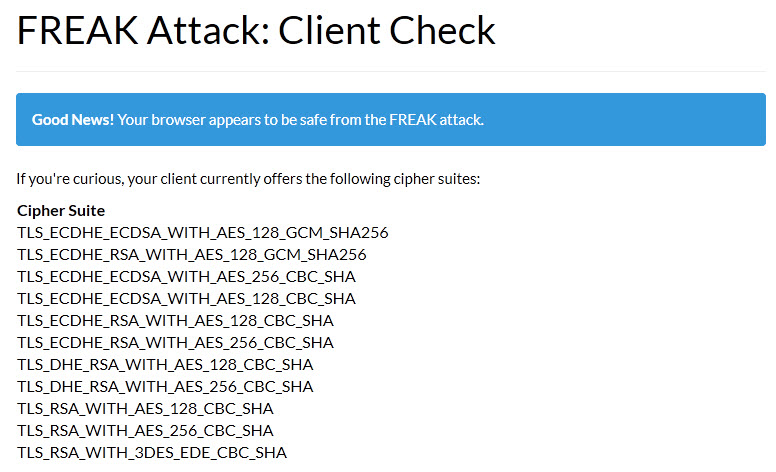
Side Tip: If you run a server that supports SSL/TLS, use this tool to check for the vulnerability. If your server is vulnerable, use Mozilla's recommended configuration to disable support for vulnerable cipher suites.
On Windows, only Internet Explorer appears to be vulnerable while all other browsers appear to be protected against exploits.
Microsoft released a security advisory yesterday that includes a workaround for some Windows systems. Some? The workaround requires access to the Group Policy Editor which is only available on Professional, Ultimate and Enterprise versions of Windows.
There is no workaround for systems that don't support the Group Policy Editor.
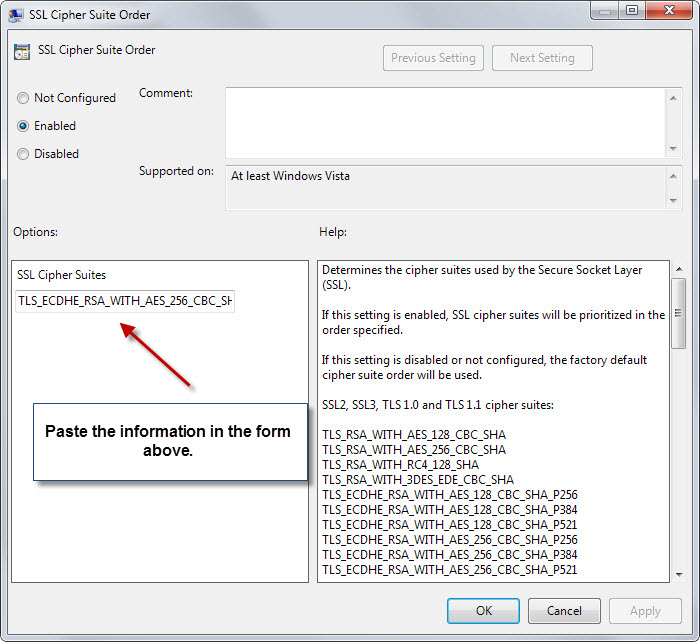
- Tap on the Windows-key and type gpedit.msc and hit enter.
- Use the left sidebar to navigate to Local Computer Policy > Computer Configuration > Administrative Templates > Network > SSL Configuration Settings.
- Double-click on SSL Cipher Suite Order.
- Switch the policy to enabled.
- Copy the Cipher suite order from Microsoft's advisory page to the clipboard, and paste it into the SSL Cipher Suites form.
- Click ok and restart the PC.
This protects Internet Explorer from the vulnerability. Windows won't connect to systems that use a cipher not supported in the list that you have added in the Group Policy Editor.
To undo the change at a later point in time, set the policy to disabled.
To mitigate the issue on Windows, use a browser that is not Internet Explorer for the meantime or apply the workaround mentioned above if possible. (via Deskmodder)
Now You: Is your system vulnerable?
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments