McAfee Raptor, a real-time behavior detection technology
McAfee just released Raptor, a real-time behavior detection technology that is available as a standalone version for 32-bit and 64-bit versions of the Microsoft Windows operating system.
Apart from being available as a standalone version, McAfee has integrated Raptor into Stinger, a standalone program that detects and remove viruses and other malicious programs from Windows systems.
If you run Raptor as a standalone version, you will first and foremost notice no change on the system. The program installs itself in C:\Program Files\McAfee\Raptor without installation dialog and runs in the background afterwards. The program folder stores log files and the quarantine as well.
The only indicator that it is running is its system tray icon and the Raptor.exe process that is listed in Windows' Task Manager and other process managers.
Raptor displays a handful of options when you right-click on its system tray icon. Use it to open the program log, quarantine or to stop it from running on the system.
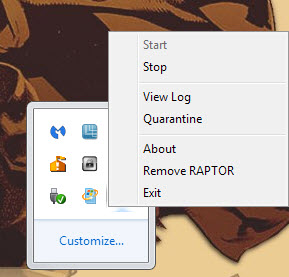
The difference between exit and remove Raptor is the following: exit terminates Raptor's process for the session while remove blocks it from starting with the operating system on the next boot.
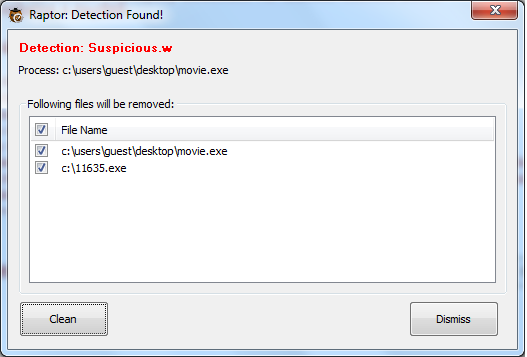
Raptor displays a dialog whenever it detects suspicious file running on the system.
A special version of McAfee's Stinger application, free to download and use as well, ships with Raptor now. You can download it from the official website where it is currently only offered as a 64-bit application.
When you run Stinger for the first time Raptor is installed automatically on the system. From there, it works just like the standalone version of the program.
The homepage reveals information about how Raptor works and what it does.
Stinger now includes Raptor - a real-time behavior detection technology that monitors suspicious activity on an endpoint. Raptor leverages machine learning and automated behavioral based classification in the cloud to detect zero-day malware in real-time.
According to McAfee, Raptor collects and submits system information to McAfee servers. This includes behavioral traces of files (typically a few bits according to the company) and trace information such as file name and path, its process ID, the version of the operating system and a random GUID of the machine.
It is too early to tell how effective Raptor is in preventing malicious 0-day programs from running on systems Raptor is installed on and how it compares to anti-exploit and other behavioral detection tools.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments