Hybrid Analysis: analyze Windows files in a browser sandbox
Whenever I find a new program to review here on this site, I run it through a series of security tests first to make sure that it is not malicious or problematic in other ways.
Services like Virustotal are indispensable for that as they scan these files using dozens of different antivirus engines. While that increases the likelihood of false positives as well, the results are useful most of the time especially if no hits are returned by the service.
If results are not clear, I run additional tests to find out more about the program before I run it on a local system.
Hybrid Analysis by Payload Security is a free malware analysis service that runs files that you upload to it in a virtual sandbox environment.
The service supports select file types only. Supported are PE (Portable Executable) formats like exe, com or dll, major Microsoft Office document formats such as docx, xlsx or pptx, and Java jar files. Common archive formats such as 7z, zip or gzip2 are supported by Payload Security on top of that.
Information about supported file types are not listed on the upload page and the service does not throw an error message immediately when you select an unsupported file for examination.
After you picked a file from the local system, you are asked to fill out a captcha and pick the analysis environment that you want used.
Four different Windows environments are provided by Payload Security:
- Windows 7 64-bit German.
- Windows 7 32-bit English.
- Windows 8.1 32-bit English.
- Windows 7 32-bit Stealthy Mode.
You may add an email address for notifications as it may take a while before the selected file is processed. This is optional however and if you keep the scan window open results are displayed on it directly once the scan completes.
The analysis is extensive and it will take a while to go through it. Hybrid Analysis displays an overall threat rating however which you may find useful.
The results page is divided into several parts. It begins with a threat assessment that lists potentially malicious, suspicious and informative behaviors.
For instance, malicious behaviors may list the dropping of a system driver or native function calls. Detailed information for each behavior are displayed listing file names and sources.
What's interesting here is that you can look up reports that match the same signature. If you do that, a list of previously scanned files are displayed which may help you in your analysis.
Extensive details about the file are displayed afterwards including various hashes, classification, version information and developer information.
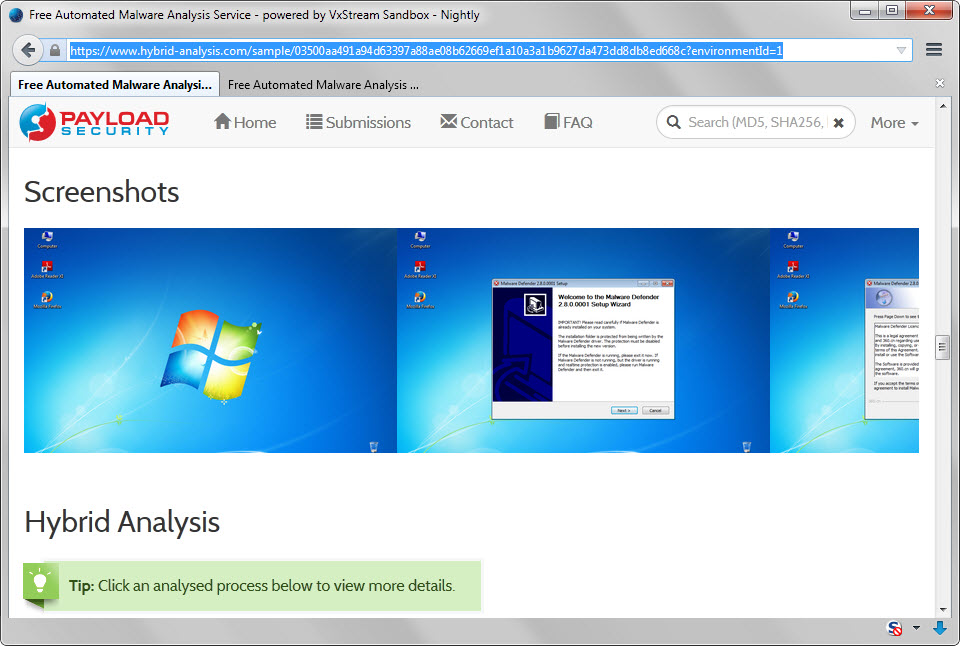
Another interesting part of the analysis is the screenshots timeline which displays various execution steps. If you add a setup file for instance, all steps of the setup are displayed as screenshots on the results page.
Network traffic, that is requests made by the program, is highlighted as well. The service divides the information into DNS requests, contacted hosts and HTTP requests. The information provided can be useful in various ways. For instance, you could block hosts or sites prior to running the program on your system or simply make sure that the connections are legitimate.
Hybrid Analysis lists the first ten files that were dropped during execution, e.g. temp files, and strings that it found in the program file.
Information like strings, network capturing files in PCAP format and a HTML report can be downloaded to the local system for further analysis or safe-keeping.
A link to Virustotal is provided on the page that lists scan results for the file on the site. Useful as the scan seems to be initiated during analysis on the Payload Security website.
The search on the service's page supports hash values that you can enter to look up past reports. What may be interesting in some cases is that you can search for IP addresses, host names or signatures as well.
Verdict
Hybrid Analysis is an advanced security tool that provides you with detailed information about supported files that you upload to the service.
While it takes some deeper understanding of Windows and program code to understand the advanced parts of the analysis, some of its features are useful to all Windows users.
This includes execution screenshots, information about network traffic or the general threat assessment rating of the file.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments