Emergency Patch for Windows vulnerability MS15-078 released (KB3079904)
Microsoft pushed out an emergency patch yesterday via automatic updates to all supported versions of its Windows operating system that patches a critical issue that could allow remote code execution when exploited successfully.
Specifically, the vulnerability exploits an issue in the Windows Adobe Type Manager Library when specially crafted documents with OpenType fonts are loaded on the system.
This may happen when users open malicious documents on the system directly or when they visit websites that use embedded OpenType fonts. Since ATM may be used by other programs besides Internet Explorer, it may affect systems where other web browsers are used to browse the Internet or open documents.
When successfully exploited, attackers can take control of the system by installing or removing programs, modifying user accounts or deleting data.
It is interesting to note that the patch replaces MS15-077 (KB3077657) which Microsoft released on July 14, 2015 which patched an elevation of privilege vulnerability in the Adobe Type Manager font driver.
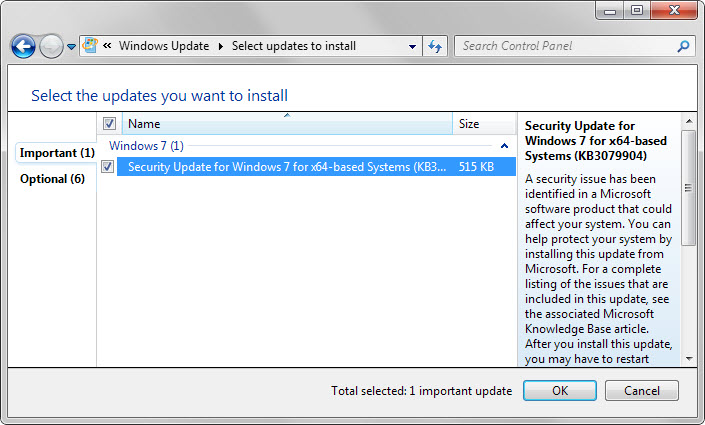
The vulnerability affects all versions of Windows including the unsupported Windows XP and Windows 2003 versions. While Windows XP did not receive any of the two patches, Windows 2003 did receive the first of the two but not the second due to EOL of support.
Microsoft Windows XP and Windows 2003 admins and users may find the manual workaround instructions helpful on the official bulletin website which they may use to protect systems from exploits. The company suggests to rename the file atmfd.dll on pre-Windows 8 systems, and to disable the Adobe Type Manager on Windows 8 or later systems.
Rename atmfd.dll on 32-bit systems
cd "%windir%\system32"
takeown.exe /f atmfd.dll
icacls.exe atmfd.dll /save atmfd.dll.acl
icacls.exe atmfd.dll /grant Administrators:(F)
rename atmfd.dll x-atmfd.dll
Rename atmfd.dll on 64-bit systems
cd "%windir%\system32"
takeown.exe /f atmfd.dll
icacls.exe atmfd.dll /save atmfd.dll.acl
icacls.exe atmfd.dll /grant Administrators:(F)
rename atmfd.dll x-atmfd.dll
cd "%windir%\syswow64"
takeown.exe /f atmfd.dll
icacls.exe atmfd.dll /save atmfd.dll.acl
icacls.exe atmfd.dll /grant Administrators:(F)
rename atmfd.dll x-atmfd.dll
Disabling atmfd on Windows 8 or later
- Tap on the Windows-key, type regedit and hit enter.
- Navigate to the key: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows\DisableATMFD
- If DisableATMFD does not exist, right-click on Windows and select New > Dword (32-bit) Value.
- Set its value to 1.
The patch that Microsoft pushed out today patches the vulnerability on all supported systems. It can be installed via automatic updates on Home systems of the operating system, or downloaded via Microsoft's Download Center. Download links for each affected operating system are provided under "affected software" on the MS15-078 support page.
Microsoft states that the vulnerability is public but that it is not aware of attacks making use of it currently. The emergency release nature of the patch indicates a high probability for the issue to be exploited in the near future.
The exploit was discovered after hackers leaked internal files of Italian company Hacking Team.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments