Lenovo once again in hot waters over Lenovo Service Engine BIOS
The year has not been good for Lenovo so far. After news broke in February that the company shipped some of its computer systems with adware and a problematic root certificate, it seemed unlikely that a major incident like this would happen again.
Recent threads on Reddit and Hacker News indicate that Lenovo used a utility it called Lenovo Service Engine in the BIOS of some products that downloaded a program called OneKey Optimizer to user systems and sent "non-personally identifiable system data" to Lenovo servers.
What makes this particularly worrisome is that Windows files were overwritten on boot, that files were added to the Windows system32 directory, and that a service was set up on the system to transfer the data to Lenovo.
The collected data, according to Lenovo, consists of machine type and model, a system UUID, region and date. Once the data has been submitted successfully the service is automatically disabled on the system.
Since the tool is based in the BIOS, it will do its work even if the Lenovo machine is formatted and Windows is installed cleanly afterwards.
Security vulnerabilities were discovered in Lenovo's implementation, which the company admits were not consistent with Microsoft's security guidelines for Windows Platform Binary Table.
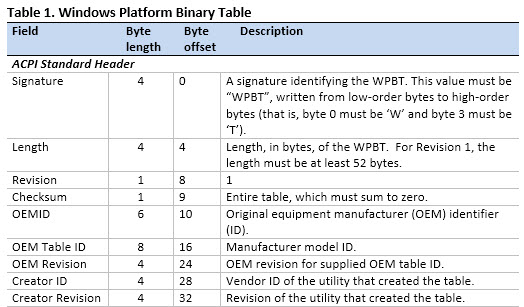
But what is the Windows Platform Binary Table?
The WPBT is a fixed Advanced Configuration and Power Interface (ACPI) table that enables boot firmware to provide Windows with a platform binary that the operating system can execute.
[..]
It is expected that the binary pointed to by the WPBT is part of the boot firmware ROM image. The binary can be shadowed to physical memory as part of the initial bootstrap of the boot firmware, or it can be loaded into physical memory by extensible boot firmware code prior to executing any operating system code.
Affected products (according to this news post)
Lenovo Notebooks: Flex 2 Pro 15 (Broadwell), Flex 2 Pro 15 (Haswell), Flex 3 1120, Flex 3 1470/1570, G40-80/G50-80/G50-80 Touch, S41-70/U41-70, S435/M40-35, V3000 , Y40-80, Yoga 3 11 , Yoga 3 14, Z41-70/Z51-70, Z70-80/G70-80
Lenovo Desktop: A540/A740, B4030, B5030, B5035, B750, H3000, H3050, H5000, H5050, H5055, Horizon 2 27, Horizon 2e(Yoga Home 500), Horizon 2S, C260, C2005, C2030, C4005, C4030, C5030,
X310(A78), X315(B85)
Lenovo Desktop (China): D3000, D5050, D5055, F5000, F5050, F5055, G5000, G5050, G5055, YT A5700k, YT A7700k, YT M2620n, YT M5310n, YT M5790n, YT M7100n, YT S4005, YT S4030, YT S4040, YT S5030
The fix
Lenovo has released BIOS updates for affected products that disable the Lenovo Service Engine, and a tool that removes services and files on systems running Windows 7, Windows 8 and 8.1, and Windows 10.
The removal tool runs the following operations on affected systems:
- Stops the LSE service
- Deletes all files installed by the LSE module, which include C:\windows\system32\wpbbin.exe,
C:\windows\system32\LenovoUpdate.exe, C:\windows\system32\LenovoCheck.exe - Repairs the autocheck files in Windows
- Disables the UEFI variable that enables LSE if the system is running Windows 8, 8.1 or 10 in UEFI mode
Downloads are provided on the Lenovo support website.
Closing Words
This is Lenovo's second major security incident this year that affects company products. While some customers may have drawn a line earlier this year when the first incident occurred, it is likely that others will do so after this second incident.
Now You: Have you bought Lenovo in the past? Will you do so in the future?
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments