Firefox Addon Detector identifies installed Firefox add-ons
Firefox Addon Detector is a web service that reveals if Firefox users connecting to the service have specific Firefox add-ons installed.
If you are using the Firefox web browser you may know that Firefox uses local resources such as images or style sheets. One simple example is about:logo which displays the Firefox logo when used as an image tag on a website but only if the website is visited using the Firefox browser.
About:logo is a reference to an image, and since it is a Firefox specific reference, it only works if the browser is used as other browsers such as Chrome or Microsoft Edge don't know about the reference or ship with the image that is linked.
One issue that arises out of this is that the scanning can be abused. First, it enables any website to identify that Firefox is being used with 100% accuracy. Second, it can also be used to identify add-ons of the browser if they reference local files.
Not all Firefox add-ons can be listed on a web page using the hack. Technically speaking, any Firefox add-on that uses the parameter contentaccessible=yes in its chrome.manifest file can.
Firefox Addon Detector
Firefox Addon Detector is a free web service that demonstrates the hack. It checks whether Firefox is the browser used to open the website and whether one or multiple of more than 400 add-ons are installed in the browser.
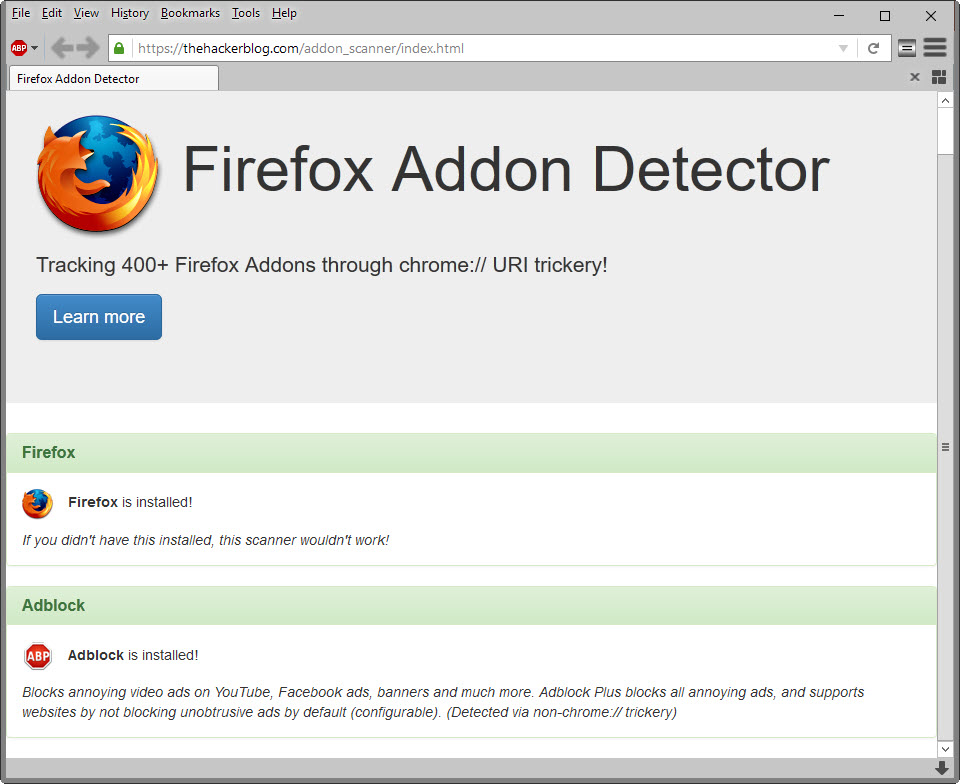
The author scanned more than 12,000 add-ons and found the flag present in more than 400 of them including popular extensions such as Adblock. While that is not a lot, considering that it is less than 4% of all add-ons, the hack is not the only one that sites can use to find out if specific add-ons are installed in the browser.
Update: The Adblock detection uses a different mechanic. It detects whether a resource that it tries to fetch is blocked, and it if is, assumes that Adblock is used based on that.
The technique is not new, and first mentions of it date back as early as 2007. Other articles mentioning it can be found here and here. The situation was worse previously and changed only after Mozilla required extension developer to explicitly use the contentaccessible parameter in the manifest file to allow local files to be referenced on remote Internet pages.
Extensions like NoScript won't help protect against this as the enumeration does not require JavaScript.
What Firefox users can do is check whether their installed extensions use the parameter so that they are at least aware of this.
The information may be used to fingerprint systems, and maybe also in attacks.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments