Microsoft launches EMET 5.5 Beta with Windows 10 support
Microsoft EMET 5.5 Beta, the Enhanced Mitigation Experience Toolkit created by Microsoft, is now available for download for all supported operating systems.
The program, designed to mitigate exploits that slipped by system defenses, has been designed as a security tool that blocks exploits from being carried out successfully on machines running Windows.
While EMET offers by no means 100% protection against all sorts of exploits -- researchers have shown in the past that it is possible to bypass some or even all of EMET's anti-exploit measures -- it is quite useful generally speaking as the majority of malicious software has not been designed to bypass EMET or other anti-exploit software such as Malwarebytes Anti-Exploit.
Microsoft EMET 5.5 Beta
The main Enhanced Mitigation Experience Toolkit website over on Microsoft's Technet site links to the latest stable version of EMET -- currently version 5.2 -- and the latest beta download that Microsoft released yesterday.
Probably the biggest change in EMET 5.5 is (official) support for Microsoft's new operating system Windows 10. While EMET 5.2 ran fine on Windows 10, it never supported the operating system officially and this changes with the new release.
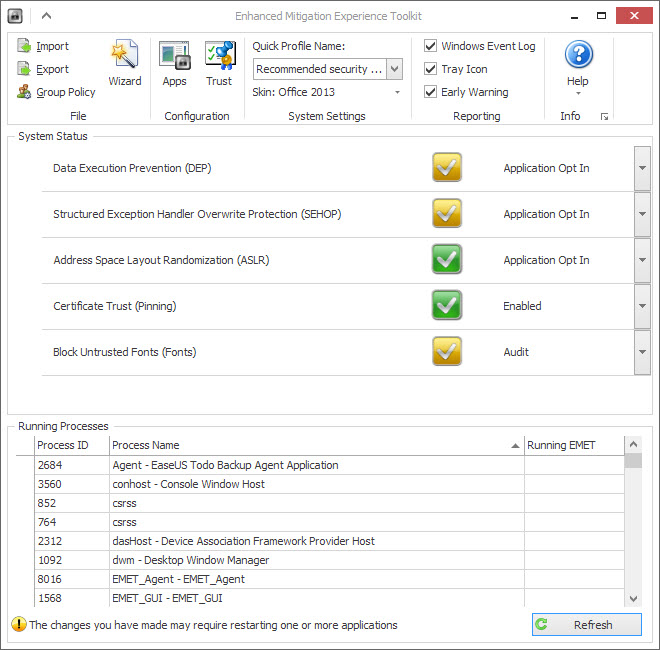
When you run the Beta version of EMET after installation you will notice another change right away, provided that you run Windows 10 and not an earlier version of Windows.
The main interface lists the new "Block Untrusted Fonts" option which is set to audit by default. This is a Windows-10 specific feature that is not supported on previous versions of Windows.
Windows 10 ships with settings to block untrusted fonts. The feature is not enabled by default, and can be set to on or audit if desired.
On prevents any font from being loaded that is not in the Fonts directory of the Windows installation, while audit writes untrusted font events to the log but won't block access to them. There is also an option to exclude apps so that they can load untrusted fonts regardless of the global preference.
Configuring untrusted fonts blocking in Windows 10
- Tap on the Windows-key, type regedit and hit enter.
- Confirm the UAC prompt if it is displayed.
- Navigate to the key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Kernel\.
- Right-click on "Kernel" and create the QWORD (64-bit) Value preference MitigationOptions if it does not exist.
- To turn untrusted font blocking on, set the value to 1000000000000.
- To turn it off again, set it to 2000000000000 or delete MitigationOptions.
- To set the feature to audit, set the value to 3000000000000.
Please note that you need to add existing mitigation values to the number. For instance, if MitigationOptions exists already on your system and is set to a value of 1000, you need to add 1000 to the value, e.g. 1000000001000 when turning the untrusted font blocking feature on.
Other EMET 5.5 improvements
The new EMET version ships with a handful of additional improvements:
- Better configuration of various mitigations via GPO.
- EAF/EAF+ pseudo-mitigation performance improvements.
- Bug fixes.
Microsoft notes that EMET 5.5 mitigations do not apply to the company's own Edge browser on Windows 10 due to " the advanced technologies used to protect Microsoft Edge, including industry leading sandboxing, compiler, and memory management techniques".
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments