How safe are security products? First AVG, now TrendMicro with major flaws
Google researcher Tavis Ormandy discovered a major flaw in the password manager component of TrendMicro Antivirus for Windows recently that had several major security issues that would, among other things, allow websites to run arbitrary commands, expose all stored passwords, or run a "secure browser" that is not secure at all.
It seems that Google is currently investigating security products on Windows, and there especially those that interact with the Chrome web browser or Chromium in one way or the other.
The company shamed AVG openly in the beginning of January for its Web TuneUp extension for Chrome as security flaws put the 9 million Chrome users who use it at risk.
TuneUp, installed with AVG security software or separately, put Chrome users at risk by disabling "web security" for Chrome users who had installed the extension.
AVG produced a fix eventually (needed two attempts for that, the first was rejected as it was not sufficient).
TrendMicro Password Manager security issue
And now it is Trend Micro that gets shamed openly by Google. According to Ormandy, the Password Manager component is the culprit this time which is installed automatically with TrendMicro Antivirus for Windows and runs on start (and also available as a standalone program and app).
This product is primarily written in JavaScript with node.js, and opens multiple HTTP RPC ports for handling API requests.
It took about 30 seconds to spot one that permits arbitrary command execution, openUrlInDefaultBrowser, which eventually maps to ShellExecute().
This means any website can launch arbitrary commands[..]
In a reply to an employee of TrendMicro Ormandy added the following information:
Hey, just wanted to check if there's any update here? This is trivially exploitable and discoverable in the default install, and obviously wormable - in my opinion, you should be paging people to get this fixed.
FWIW, it's even possible to bypass MOTW, and spawn commands without any prompts whatsoever. An easy way to do that (tested on Windows 7), would be to auto-download a zip file containing an HTA file, and then invoke it [..]
The first build that TrendMicro sent over to Travis Ormandy for verification fixed one of the major issues of the program (the use of ShellExecute), but that did not take care of other issues spotted during the rough examination of the code.
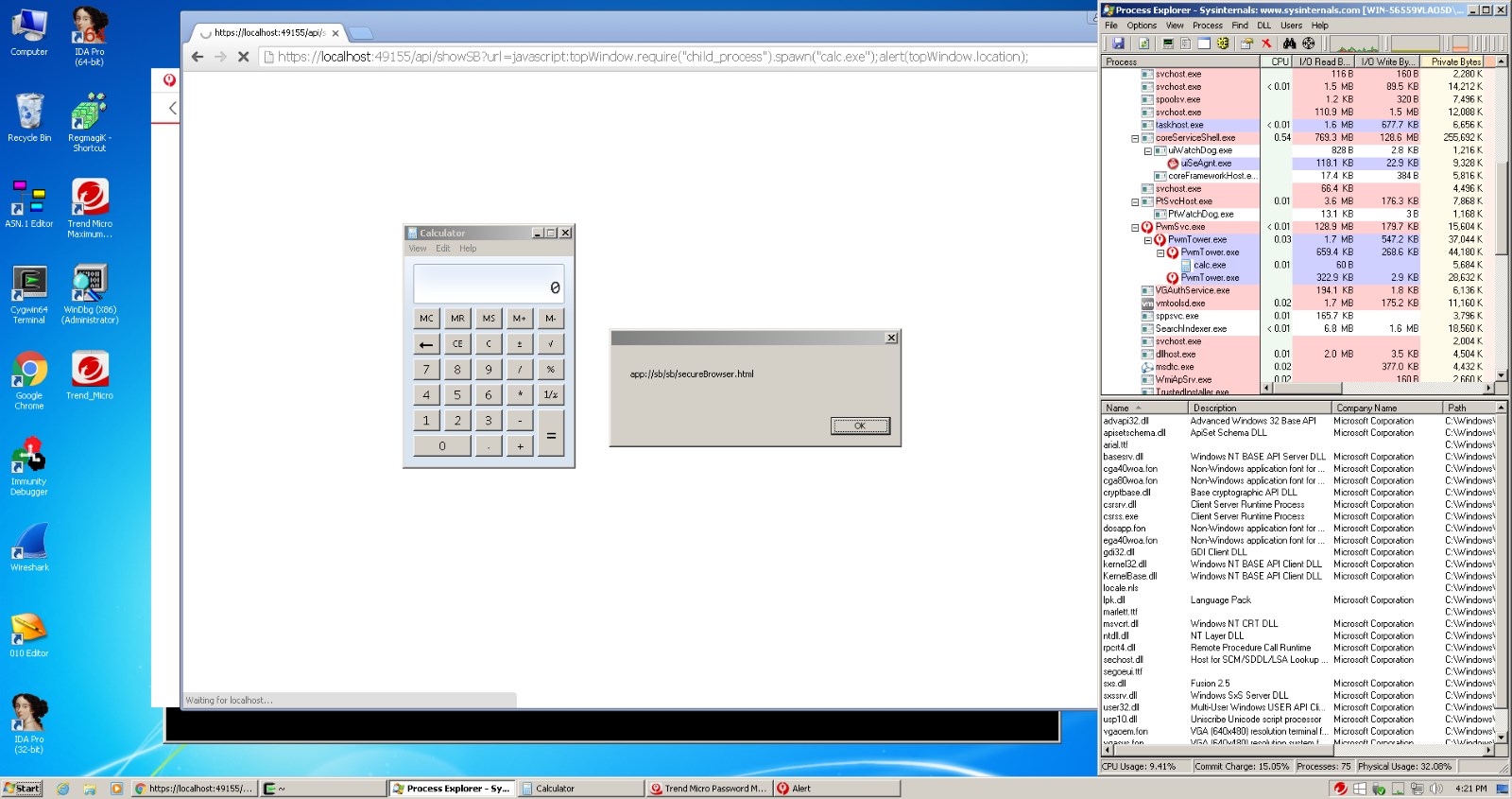
Ormandy noted for instance that one of the APIs used by TrendMicro spawned "an ancient" build of Chromium (version 41 of the browser which is now available as version 49) and that it would disable the browser's sandbox on top of that to offer a "secure browser" to its users.
His reply to TrendMicro was blunt:
You were just hiding the global objects and invoking a browser shell...? ...and then calling it "Secure Browser"?!? The fact that you also run an old version with --disable-sandbox just adds insult to injury.
I don't even know what to say - how could you enable this thing *by default* on all your customer machines without getting an audit from a competent security consultant?
Last but not least, Ormandy discovered that the program offered a "nice clean API for accessing passwords stored in the password manager", and that anyone c just read all of the stored passwords".
Users are prompted on installation to export their browser passwords, but that's optional. I think an attacker can force it with /exportBrowserPasswords API, so even that doesn't help. I sent an email pointing this out:
In my opinion, you should temporarily disable this feature for users and apologise for the temporary disruption, then hire an external consultancy to audit the code. In my experience dealing with security vendors, users are quite forgiving of mistakes if vendors act quickly to protect them once informed of a problem, I think the worst thing you can do is leave users exposed while you clean this thing up. The choice is yours, of course.
The issue appears to have not been fixed completely at the time of writing despite TrendMicro's efforts and several patches the company produced in the past couple of days.
Security software inherently insecure?
The main question that should come out of this is "how secure are security products"? Two major issues in two products by major players in the antivirus field are cause for concern, especially since there is a chance that they are not the only ones that don't seem to have secured their own products properly.
For end users, it is nearly impossible to tell that something is wrong which leaves them in a precarious situation. Can they trust their security solution to keep their data safe, or is it the very software that should secure their computers that is putting it at risk?
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments