Security Issues in Malwarebytes Anti-Malware disclosed
A recently disclosed vulnerability in Malwarebytes Anti-Malware (free, premium and enterprise) allows attackers to run man in the middle attacks against systems running the software.
Malwarebytes Anti-Malware is a popular second-opinion scanner, and the premium and enterprise editions of the program add real-time protection among other things to it which bring it more in line with traditional antivirus solutions.
The program is held in high regard by many for its malware detection and cleaning capabilities.
Google researcher Tavis Ormandy alerted Malwarebytes in early November 2015 to several security vulnerabilities that he found in Malwarebytes Anti-Malware.
Malwarebytes managed to patch several of these vulnerabilities server-side "within days", and is testing a new version of the client software internally which it plans to release in the next three to four weeks that patch the issue on the client side as well.
Ormandy discovered that the software fetches signature updates over http. While the data is encrypted, he discovered that it is easy enough for anyone to decrypt it using OpenSSL commands.
MalwareBytes fetches their signature updates over HTTP, permitting a man in the middle attack. The protocol involves downloading YAML files over HTTP for each update from http://data-cdn.mbamupdates.com. Although the YAML files include an MD5 checksum, as it's served over HTTP and not signed, an attacker can simply replace it.
Attackers have various options at their disposal to exploit the issue.
There are numerous simple ways to turn this into code execution, such as specifying a target file in the network configuration, writing a new TXTREPLACE rule to modify configuration files, or modifying a Registry Key with a REPLACE rule.
Malwarebytes confirmed the vulnerability publicly in a recent blog post revealing that it is working on a fix. The company announced the launch of the Malwarebytes Bug Bounty program offering cash bug bounties of up to $1000 for reported issues in the application.
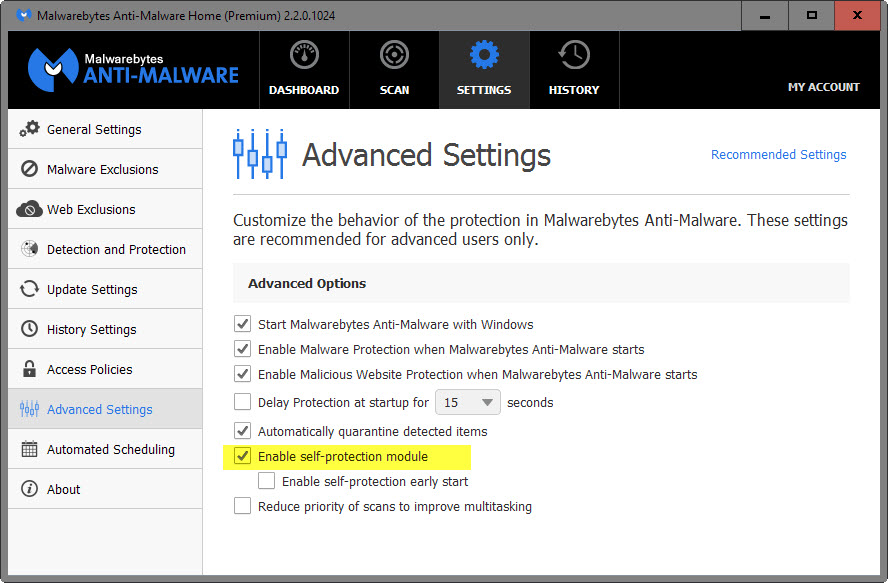
Users who run the premium or enterprise version of the application can protect it by enabling the built-in self-protect module:
- Right-click on the Malwarebytes Anti-Malware icon in the system tray and select the open option from it.
- Switch to Settings > Advanced Settings.
- Check "Enable self-protection module" if it is not enabled already.
Google's Project Zero initiative revealed vulnerabilities in products by security companies such as AVG, Kaspersky, Sophos and TrendMicro in the past.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments