When security products make systems less secure
There has been an increase in reports pf security products recently which make user systems less secure when they are installed, used or even just present on the system.
Many antivirus companies have added tools and products to their security programs in recent years to increase the perceived value of the product, add new features to them that users may find useful, and to add new revenue opportunities in form of custom search deals.
It is quite common for instance that companies deploy browser extensions on systems that change the search provider, new tab page or home page. Others have created custom versions of the Chromium browser to improve user security while the browser is being used, often calling these custom browsers secure or safe to indicate that.
Google started to analyze browser extensions and custom browsers recently and the results are quite disturbing.
The three custom Chromium-based browsers the company analyzed were found to weaken security instead of improving it.
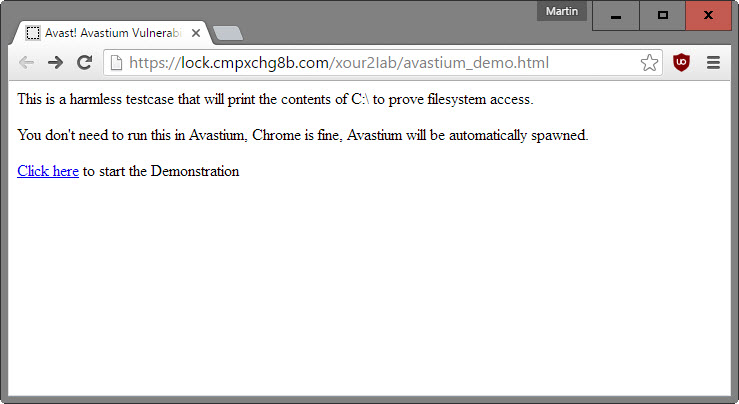
The latest company that Google contacted about security issues found in their products is Avast. The company's SafeZone browser, based on Chromium, allowed attackers to read any file on the system by getting users to click on links.
This worked even if users never used SafeZone, as data is automatically imported from a Chrome installation when the program is installed on the user system.
You don't even have to know the name or path of the file, because you can also retrieve directory listings using this attack. Additionally, you can send arbitrary *authenticated* HTTP requests, and read the responses. This allows an attacker to read cookies, email, interact with online banking and so on.
The company released an update in the meantime that fixed the issue. SafeZone is secure if you have build number 2016.11.1.2253 or newer installed.
Avast is not the only company that has been reprimanded by Google for weakening user security. Just two days ago, it was Comodo and the company's Chromodo browser, also based on Chromium, that was shamed publicly by Google.
And before that, Google revealed vulnerabilities in products by AVG, Trend Micro, Malwarebytes, and several other products as well.
While there is certainly always the possibility that software programs have security vulnerabilities, some may find it a fair assumption that these add-on products and services do more harm than good.
What weights even more is that these security companies should know better, considering that security and keeping users safe is their business.
Some companies provide users with options to customize what is installed during installation while others don't offer these options at all. It is probably a good idea to block the installation of any add-on service, browser extensions or standalone browsers, considering the findings of the past couple of months.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments