Firefox Cross-Extension vulnerability discovered
Nine of the ten most popular Firefox add-ons, based on users, are vulnerable to extension reuse vulnerabilities that allow malicious extensions to leverage these vulnerabilities.
Add-ons are one of the hallmarks of the Firefox web browser. The most popular Firefox add-ons are used by millions of users, and since the extension system in place does not limit add-on developers as much as on other platforms, some add miraculous things to the browser that are not possible elsewhere.
While researchers have analyzed the security risk associated with an "everything goes" add-on system and particular add-ons exploiting it, barely any research went into analyzing interactions between multiple extensions installed in the Firefox web browser at the same time due to a lack of extension isolation.
In the research paper CrossFire: An Analysis of Firefox Extension Re-Use Vulnerabilities, the researchers demonstrate a new class of Firefox extension attacks that exploits what they call extension-reuse vulnerabilities.
In layman terms, it is about one extension using the functionality provided by others to launch attacks.
The vulnerability relies on Firefox's current extension system, and there particularly on the fact that Firefox extensions may share the same JavaScript namespace. While Mozilla suggested in the past that extensions use unique namespaces, the security implications have not been explored for the most part.
Basically, what it means is that an extension could "read from and write to global variables defined by others, call or override all global functions, and modify instantiated objects".
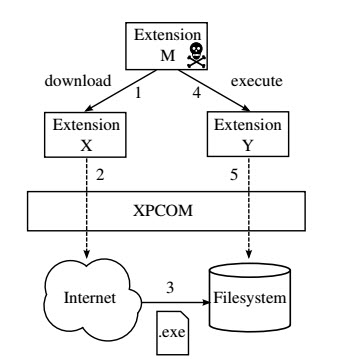
The figure shows how the malicious extension M leverages the capabilities of two legitimate extensions to download and execute code.
While malicious extensions can perform these operations as well directly, the core difference lies in the fact that these malicious extensions won't pass Mozilla's review process necessarily which means that they won't be made available on the official Mozilla Add-ons store.
The researchers note that add-ons leveraging extension-reuse vulnerabilities are harder to detect since they don't make direct calls to the APIs that enable the attack, and that it would take considerable effort by reviewers to detect malicious intent.
To demonstrate this, a Firefox add-on was developed and submitted to the Firefox add-on repository which was designed to validate HTML pages. A cross-extension call to leverage capabilities of the popular NoScript add-on was added to the add-on which connected to a URL stealthily as well leveraging a global NoScript variable.
The submitted extension passed the automated and human review process without security warnings.
According to the research, nine out of ten of the most popular Firefox extensions are vulnerable to this attack form including NoScript, Firebug, FlashGot and Web of Trust. Further analysis of a sample of 351 extensions out of the top 2000 revealed that more than 72% were vulnerable to extension-reuse attacks.
Caveats
For extension-reuse attacks to work, Firefox users need to install both the malicious extension and at least one other extension that the malicious extension exploits.
The researchers demonstrated that malicious extensions may pass Mozilla's automated and full review validation currently which increases the chance that Firefox users download and install them on their systems.
However, a new tool called CrossFire was created that automates the process of finding extension-reuse vulnerabilities in add-ons which should decrease the likelihood of that happening.
A comment by Firefox's vice president on Ars Technica highlights that Mozilla plans to introduce Firefox add-on sandboxing that the organization plans to introduce as part of its multi-process architecture implementation.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments