TeamViewer Service Outage and hacking claims
TeamViewer, the company behind the popular remote desktop software of the same name, experienced a service outage caused by a denial of service attack on the company's DNS server infrastructure on June 1, 2016.
Since then, we have seen a spike in complaints on social media sites like Twitter or Reddit from people who claim that their devices were taken over by third-parties using TeamViewer.
Statements range from user's noticing the unauthorized remote connection right away and disconnecting it, to users claiming that their PC was breached despite two-factor authentication and that the attackers managed to steal money from PayPal and other services.
TeamViewer denies that the company experienced a security breach and that the DNS issues caused by the denial of service attack are in any way related to the claims that some users are making on third-party sites.
The company points out additionally to other explanations for user system breaches and mentions explicitly password reuse and malware programs as two possibilities.
Fact is, there is has been an increase in users reporting that their devices were hacked by attackers using TeamViewer to get in.
Being a remote desktop software, attackers who successfully gain access to it can access the remote computer as if they were using it locally.
This includes opening programs, download files from the Internet, opening websites, recording passwords and other data if not protected, or opening documents and photos.
What you can do if you are using TeamViewer
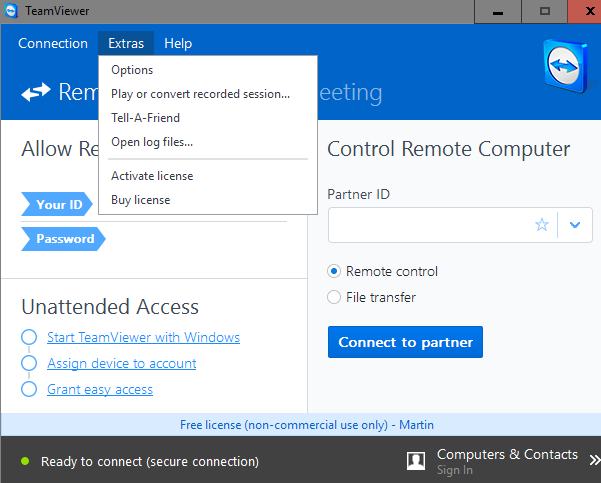
The first thing you may want to do is check the connections log.
- Windows: if you run the full client, select Extras > Open Log Files.
- Windows: if you run the Quick Support version, click on the tool symbol in the upper right corner, and select Open Logfiles.
- Linux: run the command (with root) teamviewer -ziplog.
The log files -- on Windows -- are stored in the program directory, and they are usually kept even if you remove the program from a device.
You may want to go through the log file to make sure that you recognize all remote sessions of the past three or so days.
If you have noticed a breach, you may want to be extra cautious and start changing passwords, check accounts and the account history if provided, and online accounts on sites dealing with money such as PayPal or Amazon.
If TeamViewer is running on your devices, you may want to make sure -- at least for the time being -- that the device is not left unattended. Alternatively, you may want to consider enabling TeamViewer on demand only instead of having the software run all the time. This is a precautionary measure to protect the device against hacks.
Now You: Are you using TeamViewer?
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments