Fix Firefox resource URI leak
Any website can access a selection of Firefox resource files to find out more about the web browser that is used to connect to the site.
Firefox and add-ons use the resource:// scheme to load resources internally, but some of the information are available to sites the browser connects to as well.
It is unclear why websites would need access to resource:// resources.
The leak seems to be limited to default files Firefox ships with, and not user modified files, and that is probably the main reason why Mozilla has not fixed the issue even though it was reported more than three years ago for the first time.
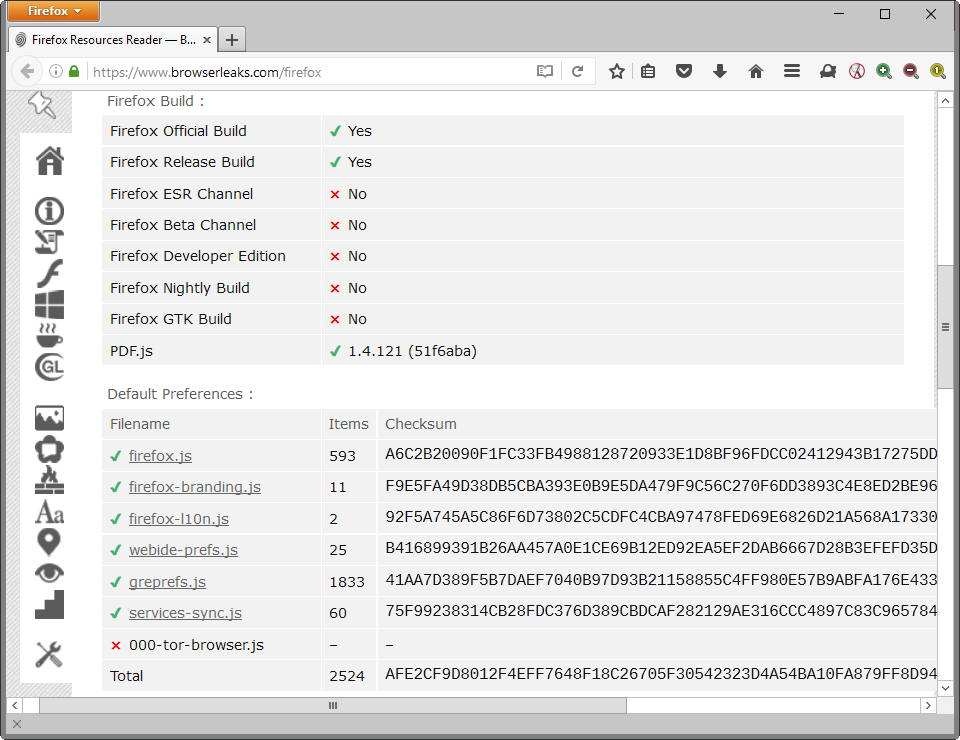
A script on Browserleaks highlights what Firefox reveals when queried by a simple script running on the site.
Please note that the script is broken in recent Nightly and Developer versions of Firefox, but that the issue remains.
The script may reveal the following information about the Firefox web browser:
- Platform the browser is run on.
- Default locale and update locale.
- Whether Tor Browser is used.
- The Firefox channel and whether it is an official build.
- If PDF.js is available and the version of the file.
- Default preference files, items listed, and their checksum (firefox.js, firefox-branding.js, firefox-l10n.js, webide-prefs.js, greprefs.js, services-sync.js, 000-tor-browser.js
The script that runs on the Browserleak website detects the locale in two ways. First, it tries to access resource:///chrome/*/locale/for all possible Firefox locales to identify the locale used.
If resource:///chrome/en-US/ is detected for instance, it means that the Firefox locale is English-US. Additionally, it attempts to access resource://gre/update.locale which reveals the Firefox interface language on all operating systems except on Linux when installed from a repository.
The script checks the file resource:///defaults/preferences/firefox.js afterwards to detect the platform, channel and other information by analyzing the file's content and comparing it to known versions of the file.
Different builds of Firefox use different sets of default preferences and settings, and that's what the leak script uses to determine platform, channel and other information.
To sum it up: websites can use a basic script currently to get information about the Firefox browser. The information are limited to platform, channel and locale.
Fix
The add-on No Resource URI Leak has been created to block websites from accessing resource files. Simply install it in Firefox to block websites from accessing resource files. The easiest way to verify that the script is indeed working is to run the Browserleak test. If it returns no information, the add-on works as intended.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments