Selfrando improves Tor Browser security
Selfrando is a new protective feature of the Tor Browser that improves the web browsers defense against hacking attempts and the de-anonymization of users.
Tor browser is a popular tool for remaining anonymous on the Internet. It is used by journalists and activists, and regular users as well to do things on the Internet anonymously.
This makes the browser a high profile target for nation states and hackers. While the Tor Browser's user count is relatively small compared to popular web browsers like Chrome or Firefox, it is based for the most part on Firefox code which is used by hundreds of millions of users.
Selfrando
Researchers from the German university of TU Darmstadt and the University of California Irvine have created a new protection for Tor called Selfrando.
Selfrando randomizes the code of the Tor browser to make it harder for attackers to know where code is on the computer the program is executed on.
The researchers mention the attack used by the FBI against Tor users specifically in the research paper.
In this paper, we present selfrando—an enhanced and practical load-time randomization technique for the Tor Browser that defends against exploits, such as the one FBI allegedly used against Tor users.
The defensive security feature attempts to prevent code-reuse exploits. These exploits use existing code for malicious purposes and are usually not stopped by common anti-exploit features such as ASLR, or Write or Execute.
The researchers have published a research paper, Selfrando: Securing the Tor Browser against
De-anonymization Exploits, that goes into great technical detail.
It is a good read if you are interested in the security concept used by Selfrando, and its implementation in the Tor browser.
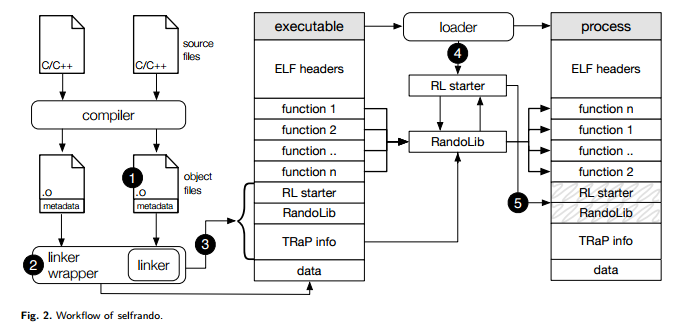
Selfrando is a framework that randomizes the program binary on load time.
For these reasons, we decided to develop a framework which makes the program binary randomize itself at load time.
Rather than modifying the compiler or linker, we developed a small tool which wraps the system linker, extracts all function boundaries from the object files used to build the binary, then appends the necessary TRaP information to the binary itself.
The new security feature is not yet available in stable builds of the Tor web browser. It is being tested in the latest nightly hardened builds which are only available for Linux currently. A version for Linux is in development but it is not clear right now when it will be available.
Selfrando may make it into Tor Browser 6.5 if testing goes well, but the more likely release version is Tor Browser 7.0 which will be out next Spring.
It is interesting to note that Selfrando could come to the Firefox web browser as well as it is not a Tor specific framework. If that happens, security of the Firefox web browser would improve as well as a consequence.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments