Sysmon 5 brings Registry modification logging
Sysmon 5 is the latest version of the popular monitoring program for Windows that writes activities to the Windows Event log.
Sysmon, which stands for System Monitor, is a background monitor. This means that it will do its work once installed without user interaction or graphical user interface.
In fact, all you have to do to install it is to run a short command from the command line to install the monitoring service.
This is done by tapping on the Windows-key, typing cmd.exe, holding down the Shift-key and Ctrl-key before hitting the Enter-key, and typing sysmon -accepteula –i in the Sysmon program directory.
Tip: to uninstall Sysmon again, run the operation again but this time with the command sysmon -u.
The program logs directly to the Windows Event log which means that you need to open it using the native viewer or a third-party program such as Event Log Explorer to access the data.
Sysmon 5
All events that Sysmon 5 tracks are stored in Applications and Services Logs/Microsoft/Windows/Sysmon/Operational in the Event log.
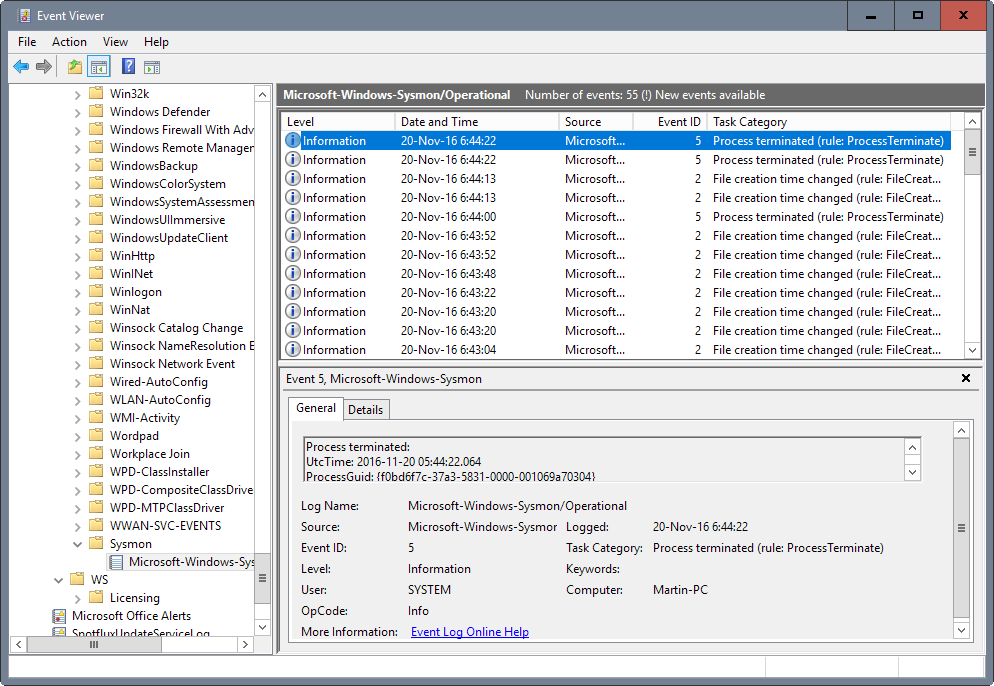
The following events are tracked by the application:
- Event 1: Process creation -- any new process that is created on the system is listed under this event ID.
- Event 2: File creation time changes.
- Event 3: Network connections -- disabled by default. To enable it, run the install command with the parameter -n.
- Event 4: Sysmon service state changes.
- Event 5: Process terminated.
- Event 6: Driver loaded.
- Event 7: Image loaded. This is disabled by default. To enable it, run the install command with the parameter -l.
- Event 8: Create Remote Thread -- logs when a process creates a thread in another process.
- Event 9: Raw Access Read -- logs when a process uses reading operations from the drive using \\, and \.
- Event 10: Process Access -- Logs when a process opens another process.
- Event 11: File Create.
- Event 12: Registry Event (Object Create and Delete) -- Logs when processes create or delete Registry objects.
- Event 13: Registry Event (Value Set) -- Logs when processes set values in the Registry.
- Event 14: Registry Event (Key and Value rename) -- Logs when Registry keys or values are renamed.
- Event 15: File Create Stream Hash -- Logs when a file stream is created.
- Event 255: Error.
Filtering is supported which means that you can use Event Filtering to filter for specific events you are interested in.
The new Sysmon 5 introduces new monitoring options that log file create and Registry modification events.
This major update to Sysmon, a background monitor that records activity to the event log for use in security incident detection and forensics, introduces file create and registry modification logging. These event types make it possible to configure filters that capture updates to critical system configuration as well as changes to autostart entry points used by malware.
Closing Words
Sysmon 5 improves an already great program further by introducing Registry modification and file create events to the logging capabilities. Since nothing else has changed, it is a no brainer to upgrade the existing copy of the program to the latest version to benefit from the additional event logging options.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments