Flash tops the Exploit Kits Chart in 2016 again
If you needed another reason not to use Flash anymore, a new security report by Recorded Future may convince you to consider this at the very least.
The company analyzed 141 exploits kits that were available between November 16, 2015 and November 15, 2016.
The main takeaway of the research study is that Adobe Flash vulnerabilities made up six of the top ten chart spots.
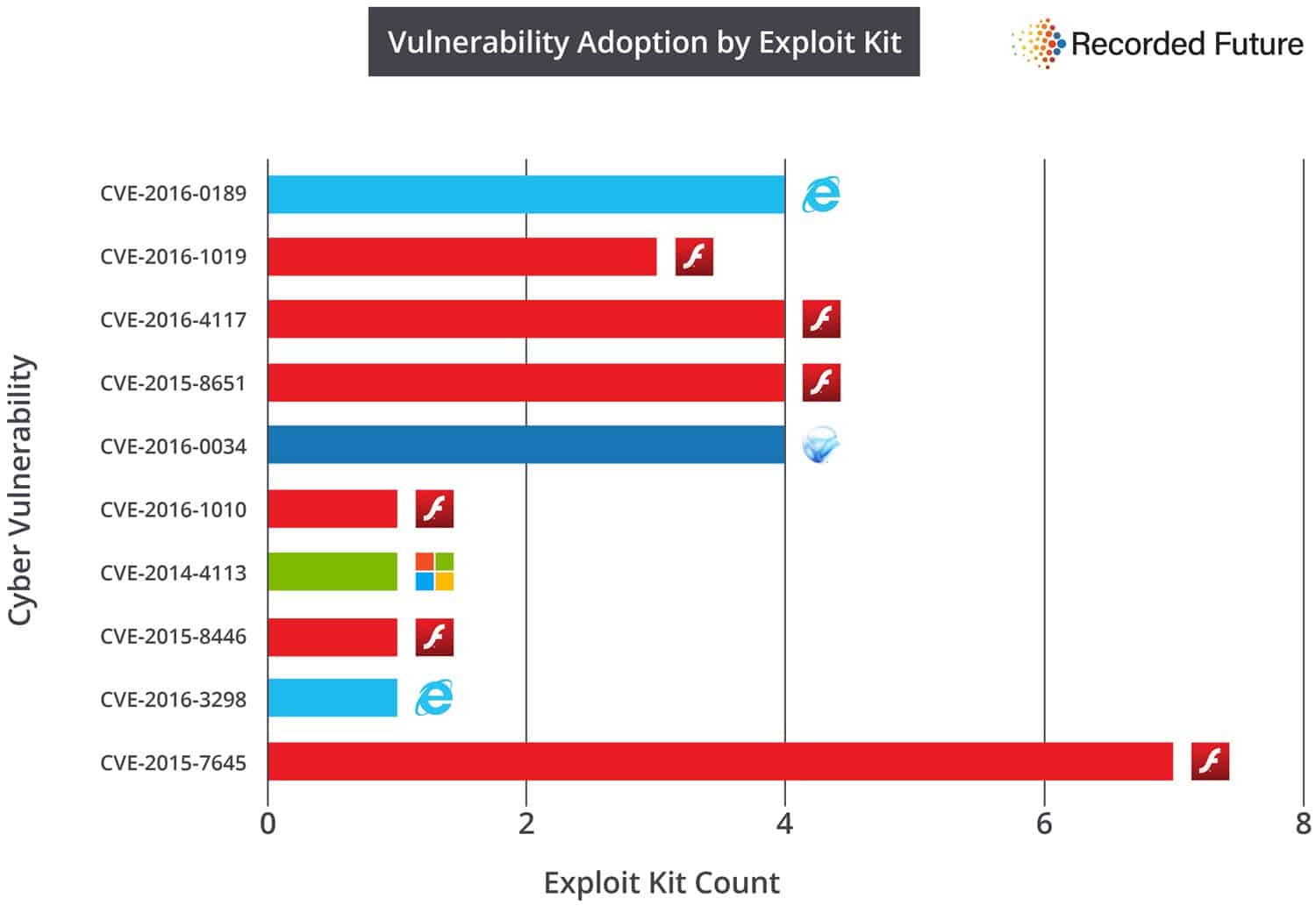
Flash was not the only software that exploit kits targeted in the past year though. In fact, a vulnerability in Microsoft Internet Explorer tops the chart, followed by three Flash vulnerabilities and then a Microsoft Silverlight vulnerability.
A Windows vulnerability comes in at seven, and another Internet Explorer vulnerability at nine. The remaining places are all filled by Flash vulnerabilities
Flash did better this year than last year. Last year, Flash topped the first eight places of the top ten vulnerabilities list used by exploit kits, with Internet Explorer and Silverlight taking up the last two spots.
As far as the methodology is concerned that Recorded Future used to generate the report: it did not reverse engineer exploit kits or use other forms of direct analysis. Instead, it used meta information available on the Internet to compute the information.
Recorded Future did not reverse engineer any malware mentioned in this analysis and instead performed a meta-analysis of available information from the web. Exploits for dozens of other vulnerabilities are currently employed by EKs and this report’s intent is to highlight top targets of popular exploit kits.
This means that the vulnerabilities are not necessarily graded by severity, or impact on user systems. Instead, the vulnerabilities are graded by references made to them on security sites, forums and such.
This can be easily seen by looking at the vulnerability adoption by exploit kit chart that the company created.
While the first five vulnerabilities listed were all exploited by three or four exploit kits, it was the Flash vulnerability in the tenth spot that was exploited the most (seven times).
The report ends with recommendations. These include the usual: patch your system and software, remove software if it is not required for core business processes, enable click to play, use script blockers, create frequent back ups, and use Chrome if possible.
The top 10 vulnerabilities
CVE-2016-0189 -- The Microsoft JScript 5.8 and VBScript 5.7 and 5.8 engines, as used in Internet Explorer 9 through 11 and other products, allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka "Scripting Engine Memory Corruption Vulnerability
CVE-2016-1019 -- Adobe Flash Player 21.0.0.197 and earlier allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via unspecified vectors, as exploited in the wild in April 2016.
CVE-2016-4117 -- Adobe Flash Player 21.0.0.226 and earlier allows remote attackers to execute arbitrary code via unspecified vectors, as exploited in the wild in May 2016.
CVE-2015-8651 -- Integer overflow in Adobe Flash Player before 18.0.0.324 and 19.x and 20.x before 20.0.0.267 on Windows and OS X and before 11.2.202.559 on Linux, Adobe AIR before 20.0.0.233, Adobe AIR SDK before 20.0.0.233, and Adobe AIR SDK & Compiler before 20.0.0.233 allows attackers to execute arbitrary code via unspecified vectors.
CVE-2016-0034 -- Microsoft Silverlight 5 before 5.1.41212.0 mishandles negative offsets during decoding, which allows remote attackers to execute arbitrary code or cause a denial of service (object-header corruption) via a crafted web site.
CVE-2016-1010 -- Integer overflow in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors
CVE-2016-4113 --Unspecified vulnerability in Adobe Flash Player 21.0.0.213 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors
CVE-2015-8446 -- Heap-based buffer overflow in Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allows attackers to execute arbitrary code via an MP3 file with COMM tags that are mishandled during memory allocation
CVE-2016-3298 -- Microsoft Internet Explorer 9 through 11 and the Internet Messaging API in Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allow remote attackers to determine the existence of arbitrary files via a crafted web site.
CVE-2015-7645 -- Adobe Flash Player 18.x through 18.0.0.252 and 19.x through 19.0.0.207 on Windows and OS X and 11.x through 11.2.202.535 on Linux allows remote attackers to execute arbitrary code via a crafted SWF file, as exploited in the wild in October 2015.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments