Researchers develop cross-browser fingerprinting technique
Researchers have developed a cross-browser fingerprinting technique that uses operating system and hardware level features.
Fingerprinting has been limited for the most part to individual web browsers in the past. If a user switched browsers regularly, fingerprinting could not be used to link the user to these browsers.
Fingerprinting tests like the Electronic Frontier Foundation's Panopticlick or BrowserPrint, try to gather data about the browser and underlying operating system. They use all the data to create a fingerprint of the browser/computer combination, and may be able to do the same in future sessions.
Cross-browser fingerprinting was out of the picture up until now. While other methods existed to track users across browsers, for instance by requiring them to sign into accounts to use a service or recording IP addresses, no fingerprinting method came close to providing a working solution.
Cross-browser fingerprinting
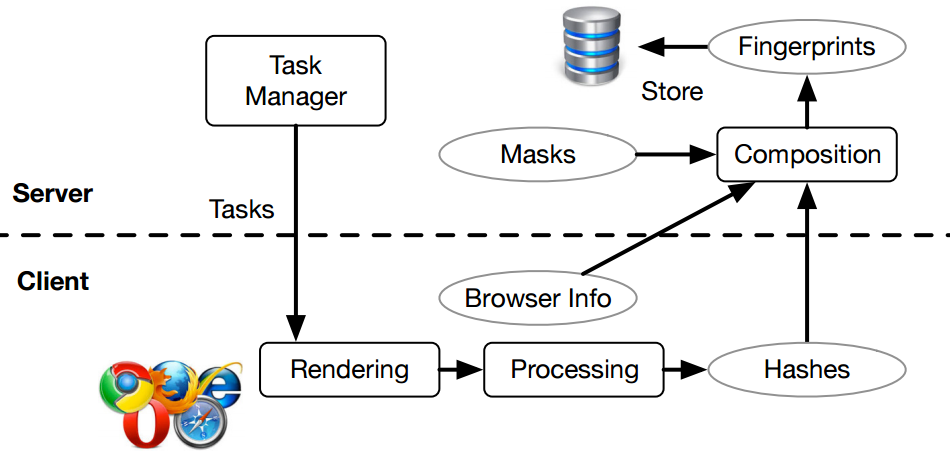
The researchers who published the research paper (Cross-)Browser Fingerprinting via OS and
Hardware Level Features think that they have found a way.
In the paper, we propose a (cross-)browser fingerprinting based on many novel OS and hardware level features, e.g., these from graphics card, CPU, audio stack, and installed
writing scripts. Specifically, because many of such OS and hardware level functions are exposed to JavaScript via browser APIs, we can extract features when asking the browser to perform certain tasks through these APIs. The extracted features can be used for both single- and cross-browser fingerprinting.
They have created an online service that demonstrates the fingerprinting technique. It is called Unique Machine, and works on any device that supports JavaScript.
A click on Get My Fingerprint starts the process. It works, if JavaScript is enabled, and if connections to a few sites are allowed. The scan takes a couple of seconds to complete.
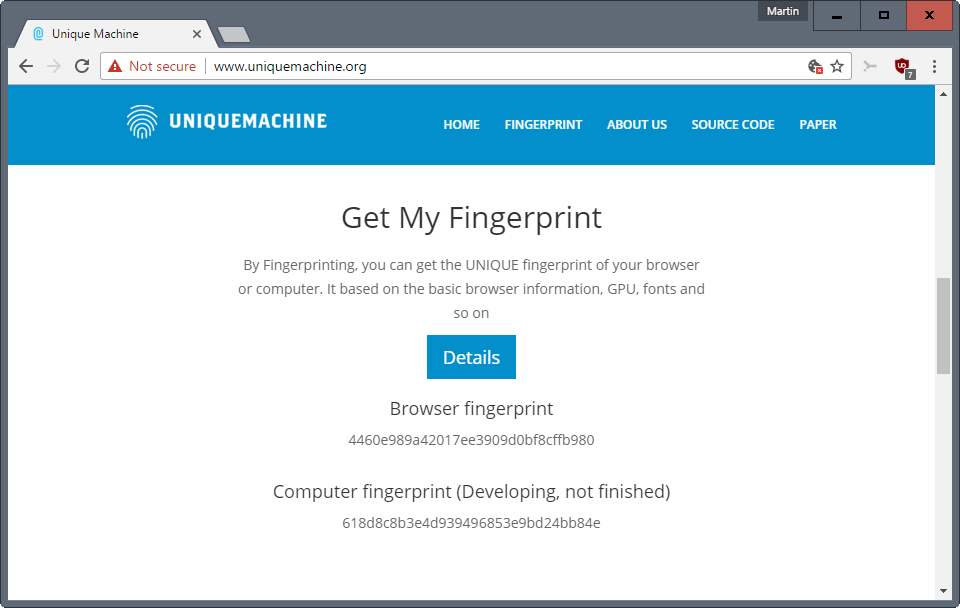
The result is a browser fingerprint, and also a computer fingerprint; the latter is not finalized yet and still in development.
You may hit the details button on the Unique Machine website for the list of tested cross-browser features.
The following features are tested currently:
- Time Zone.
- Number of CPU Cores.
- Fonts.
- Audio.
- Screen Ratio and depth.
- WebGL.
- Ad Blocking.
- Canvas.
- Cookies.
- Encoding.
- GPU.
- Hash values of GPU rendering results.
- Language.
- Plugins.
The idea is now that you will get similar results when you use a different browser on the same system to run the fingerprinting test a second time.
The researchers state that the technique identified 99.2% of users correctly. The sample size is a bit small, 1903 users and 3615 fingerprint samples.
I ran tests on a machine using different browsers, and results were mixed. The computer fingerprint was identical when I ran the fingerprinting test in Chrome, Chrome Canary and Vivaldi, but different in Firefox and Edge.
The three browsers the hash was identical in are all based on Chromium. This is probably the reason why the fingerprint was identical.
The source code of the cross browser fingerprinting site is available on GitHub.
Now You: Did your cross-browser fingerprinting work on your devices?
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments