Get File hashes using Windows PowerShell
Getting file hashes can be quite useful. This can be used for instance to make sure that backed up files are not corrupt or modified (by generating hashes before and after the process), or to make sure that no one tampered with an important file.
You may see it on download sites as well, but the use there is limited. The reason is simple: if an attacker managed to change the download file, there is a chance that the website was compromised as well. This could theoretically at least mean that the file hash displayed on the site was modified as well to fit the new malicious version of the download.
Get File hashes using Windows PowerShell
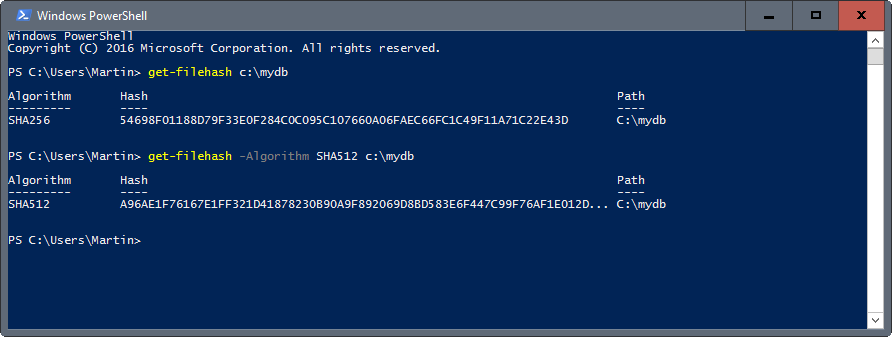
If you need to generate the hash of a file quickly on a Windows machine, then you may also use PowerShell for that.
It may not be as comfortable as some of the hashing programs out there, but it is a native implementation that does not require third-party software to work. Useful in restricted environments for instance, or when there is no Internet connection available to download these programs.
Hash generating was integrated into PowerShell 4.0. It is included in Windows 8.1 and Windows Server 2012 R2, and also available for Windows 7 Service Pack 1, Windows Server 2012, and Windows Server 2008 R2 Service Pack 1.
- Tap on the Windows-key, type PowerShell, and hit the Enter-key to start it up.
The main command is get-filehash FILEPATH, e.g. get-filehash c:\test.txt.
Get-FileHash uses the Sha256 algorithm by default. You may specify a different algorithm instead using the -Algorithm parameter.
Supported are: SHA1, SHA256, SHA384, SHA512, MACTripleDES, MD5, RIPEMD160
Note that MD5 and SHA1 are not considered secure anymore but are still supported.
So, to generate a Sha512 hash you would use the command get-filehash -Algorithm Sha512 c:\test.txt.
You may also use -LiteralPath or -InputStream instead of the default path option.
- LiteralPath: get-filehash -LiteralPath -Algorithm SHA512 c:\test.txt.
- InputStream get-filehash -InputStream -Algorithm SHA512 Stream.
The core difference between path and literalpath is that literalpath supports no wildcards, and is used exactly as it is typed.
CertUtil
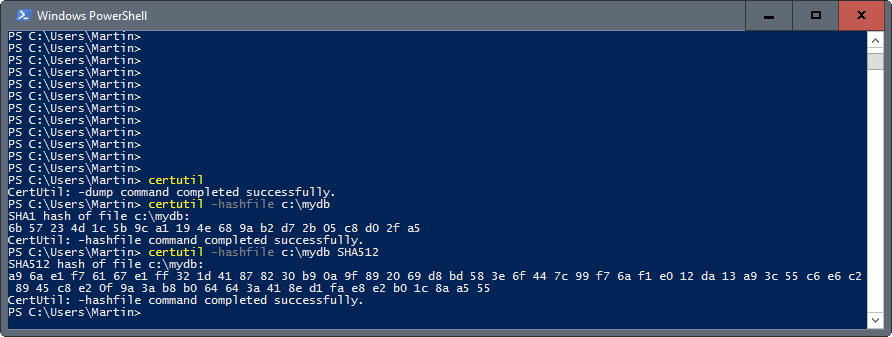
CertUtil is another native Windows program that you may use to compute hashes of files. You can run the program from the command prompt, or using PowerShell.
The base command is certutil -hashfile PATH, e.g. certutil -hashfile c:\example.txt.
You may specify the hash algorithm as well. Supported are MD2, MD4, MD5, SHA1, SHA256, SHA384, SHA512. The default algorithm is MD5.
To use a different hash algorithm, specify it after the command, e.g. certutil -hashfile c:\example.txt SHA512.
Closing Words
You may use the commands in scripts to compute hashes for several files in one operation. The two native tools get-filehash and certutil are quite handy for the quick computation of hashes on Windows, and also for script use.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments