Firefox to get option to verify all binaries to protect against compromise
Mozilla is working on a new security project for Firefox, called Binary Transparency, currently to allow all Firefox users to verify the binary files of the web browser to ensure that the files are safe and have not been tampered with.
Firefox is an open source project. This means that anyone may build the browser from source, and even change code before that.
Most Firefox users however don't do that. They download pre-compiled versions of the web browser that they download from Mozilla's own website, third-party sites, or even -- once installed -- using the automatic update feature of the web browser.
Binary versions of Firefox don't come with any assurance that they correspond to the Firefox source code of that particular version of the browser. While users could in theory build Firefox from source to compare the downloaded binary version of Firefox with the version compiled from source, it is not really something that is very practical.
Also, if you have the tools and knowledge to build Firefox from source, there is really no need to download the binary of the browser in first place.
Firefox: Binary Transparency
Mozilla plans to change that by adding a feature to the Firefox web browser that allows anyone to verify that the binary files are genuine and not compromised.
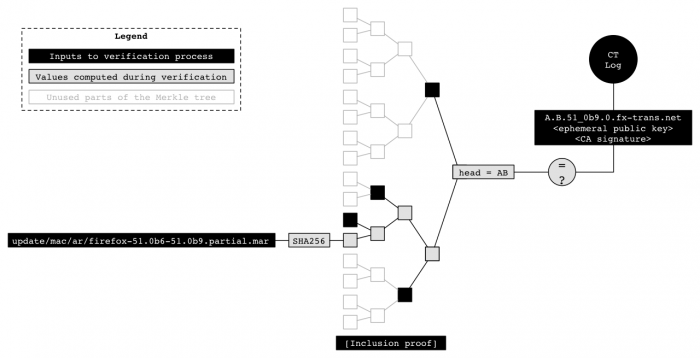
The main idea is to log all Firefox binaries in a publicly verifiable log. Anyone may look it up, and compare the binary files of the local Firefox installation with the log data to make sure that the files are the same that any other user of the web browser got during download.
While that is already helpful, plans are underway to implement that functionality in the Firefox updater as well. This means that Firefox's automatic update feature will verify any new update that it discovers before it is downloaded or installed on the user system.
Mozilla details the logging and verification steps on the official Wiki entry of Binary Transparency. The process is technical, but it uses certificates, SHA256 hashes, a Merkle tree and unique domain names for each release. You can check out the details on the wiki page if you are interested in additional details.
The verification process at its core requires that you verify one, some or all binary files of the release against the hash values of the public log file of that release. Again, there is more to the process than just described, so head over to the wiki for details on that as well.
You may be interested in the meta tracking bug over on Bugzilla, as it highlights the progress made to implement the feature. A target milestone has not been announced yet.
While you can use the feature to check Firefox binaries before download or updates, the feature may prove useful as well to check existing installations of the web browser.
Now You: What's your take on Binary Transparency?
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments