Chrome extension CopyFish hijacked: remove now!
The makers of the popular Chrome and Firefox extension Copyfish announced yesterday that the Chrome version of the extension was hijacked.
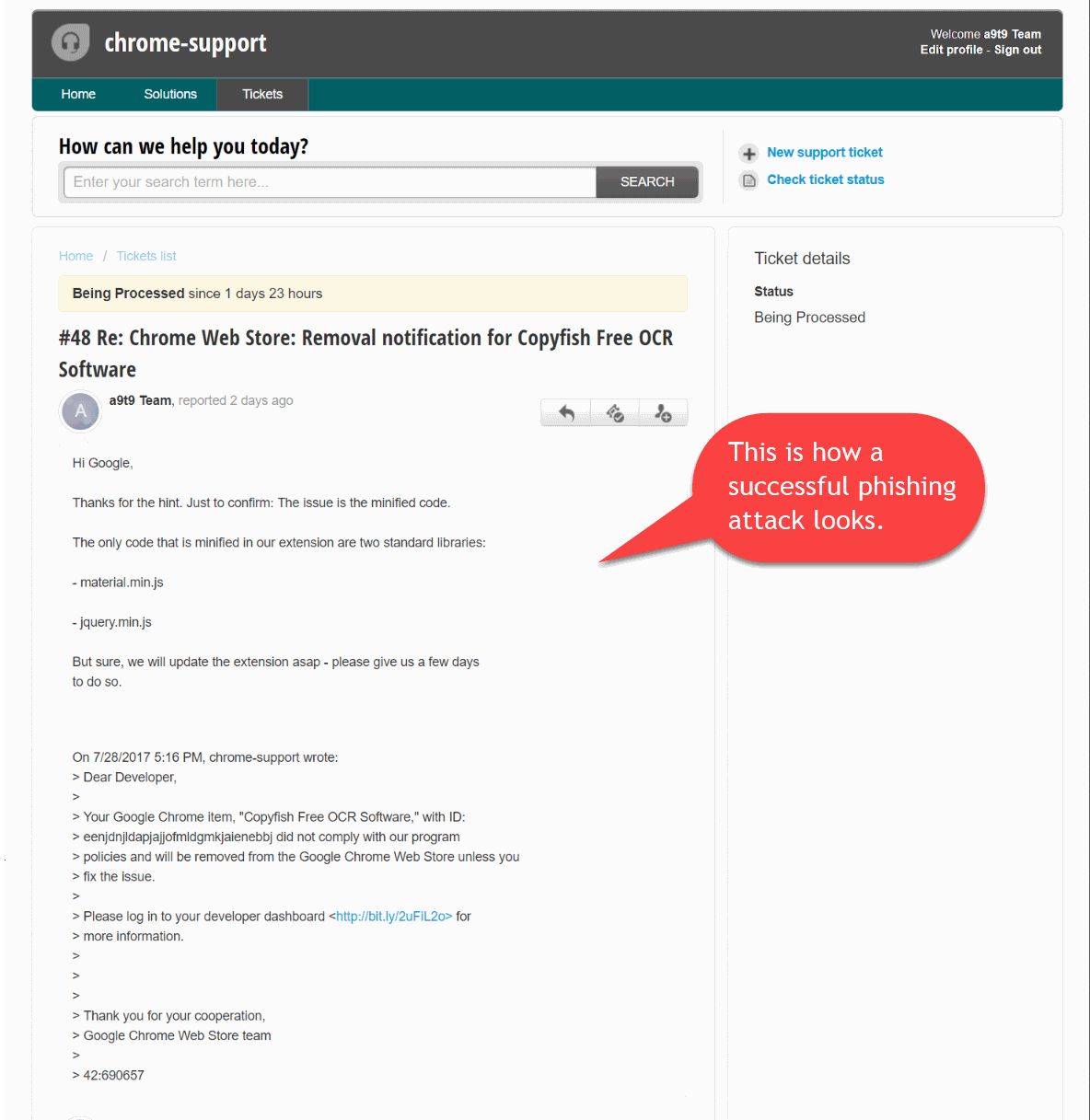
According to the posted information on the company blog, an attacker managed to steal the Google password of a team member using phishing on July 28th, 2017.
A team member received an email from “Google” saying that we need to update our Chrome extension (Copyfish) otherwise it would be removed from the store. “Click here to read more details” the email said. The click opened the “Google” password dialog, and the unlucky team member entered the password for our developer account.
The Chrome extension was updated to version 2.8.5 then the next day; something that the company did not realize directly. The attacker, who held the password and email address for the developer account, pushed a manipulated extension to the Chrome store.
Since Chrome extension update automatically without user interaction, the majority of users of the extension received the updated version. While it is possible to take precautions before installing Chrome extensions, there is no such option for extension updates.
Reports began to come in on July 30, 2017 that Copyfish for Chrome was displaying ads and spam on websites.
The team realized that something was wrong. A check of the Google Developer account revealed that the attackers did not only upload a malicious version of the extension, they moved the extension to their account as well.
This means that Copyfish has no access to the extension at this point in time. They cannot update it, and the attackers may push out another version of the extension to the userbase. Since Chrome extensions update automatically, it can only be prevented by removing the extension for Chrome for the time being.
Chrome users who have Copyfish installed right now are advised to remove the browser extension from the web browser until the situation is resolved.
This is done by loading chrome://extensions/ in the browser's address bar and activating the trash icon next to the extension.
The Firefox extension Copyfish is not affected, and there are several reasons for that. The most obvious one is that the attackers phished the Google account password and not necessarily the Mozilla account password. While it may be identical, it does not have to be.
More importantly from a user perspective is that Mozilla employees audit extension uploads manually while Google uses automation for that. It is far more difficult to place a malicious extension in Mozilla AMO than it is on Google's Chrome web store.
Phishing attacks, especially targeted ones, are still very successful. While the company could have better security processes, e.g. using two-factor authentication or a password manager to prevent having to enter account passwords manually, it is taking responsibility by explaining exactly what has happened and what users can do to resolve the issue.
It is interesting to note that Copyfish is not the first Chrome extension that got hacked successfully in recent time. Social Fixer, another popular extension, was hacked as well and the methodology the author describes on Facebook looks very similar to the one used to attack Copyfish.
Closing Words
Google's convenient but weak -- from a security point of view -- automatic updating of Google Chrome and Chrome extensions, and the company's refusal to spend resources on manual extension audits, is a serious flaw in a browser heralded for its security.
I guess it is less of a problem for users who don't use extensions, but if you do in Chrome, attacks like this will happen and there is nothing that you, as a user, can do about it if you use extensions.
If the maker of an extension gets phished or hacked, malicious extension updates may be pushed to your Chrome version and computer without you being able to do anything about that.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments