Protect Windows against Speculative Store Bypass exploits
It has become quite time consuming to stay up to date with the ever increasing threats that Spectre and Meltdown pose to computer systems around the world.
New variants pop up regularly, and manufacturers like Intel and AMD, and software developers like Microsoft, release advisories, updates, and instructions regularly for some but not all hardware or software that are affected potentially.
While you have probably done a bit of patching already to protect against some variants, you are not done yet.
Microsoft updated an advisory on today's Patch Day that includes instructions on enabling protection against Speculative Store Bypass Disable (SSBD) in Intel and AMD processors.
The update requires that microcode or firmware updates are installed on target machines running Intel processors. AMD systems don't require microcode updates according to Microsoft.
What you need to do to install the updates is the following therefor:
- Install the June 2018 security updates for your operating system (client and server supported, see chart below).
- Install the firmware or microcode update for Intel machines when released by Intel.
- Modify the Registry to enable the protection.
Question is: should you enable the protection? Microsoft did not enable it by default but revealed that it will enable the protection automatically if it notices exploits that are in the wild.
Installing the update won't affect performance according to Microsoft but enabling the protection in the the Registry will have an impact on the device's performance; this is the most likely reason why Microsoft did not enable the protection by default.
The following table shows the vulnerabilities and their default state on all supported versions of Windows.
| Operating System | CVE-2017-5715 | CV-2017-5754 | CVE-2018-3639 |
|---|---|---|---|
| Windows 10 | Enabled by default | Enabled by default | Disabled by default - see ADV180012 |
| Windows Server 2016 | Disabled by default - see KB4072698 | Disabled by default - see KB4072698 | Disabled by default - see ADV180012 |
| Windows 8.1 | Enabled by default | Enabled by default | Not applicable |
| Windows Server 2012 R2 | Disabled by default - see KB4072698 | Disabled by default - see KB4072698 | Disabled by default - see ADV180012 |
| Windows RT 8.1 | Enabled by default | Enabled by default | Not applicable |
| Windows 7 | Enabled by default | Enabled by default | Disabled by default - see ADV180012 |
| Windows Server 2008 R2 | Disabled by default - see KB4072698 | Disabled by default - see KB4072698 | Disabled by default - see ADV180012 |
| Windows Server 2008 | Enabled by default | Enabled by default | Not applicable |
To enable the Speculative Store Bypass protection in Windows, do the following:
Note: We recommend that you backup the Registry or create a system backup before you run these commands.
- Open an elevated command prompt by clicking on Start, typing cmd.exe, holding down the Shift-key and the Ctrl-key, before selecting the Command Prompt result.
-
Do the following on AMD systems:
- Run reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 64 /f
- Run reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
-
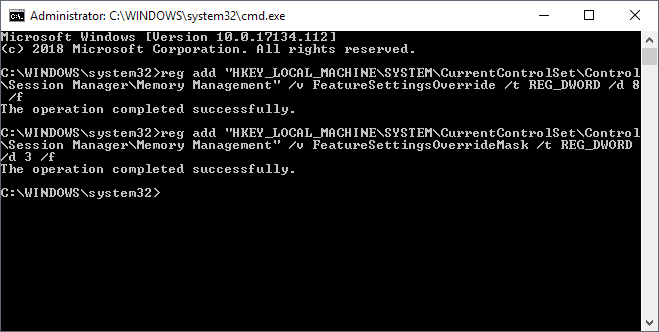
To protect against Speculative Store Bypass run the following commands:
- reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 8 /f
- reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
- Restart the PC.
To undo the protection outlined under 3) above run the following from an elevated command prompt:
- reg delete "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /f
- reg delete "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /f
See KB4073119 for additional information or updates.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments