VeraCrypt encryption software review
VeraCrypt is an encryption software that is a fork of the discontinued TrueCrypt encryption software. It can best be described as a continuation of TrueCrypt that supports all features that TrueCrypt supported plus a set of improved or new features.
Since it is based on the popular application it supports options to create encrypted containers, encrypt entire hard drives and to encrypt the system partition of the computer system. The popular option to create hidden encrypted volumes is supported as well.
VeraCrypt is an open source program that is available for Windows, Linux, Mac OS X and FreeBSD; developers and researchers can download the source code from the project website as well.
Note: The current version of VeraCrypt is 1.23. This review is based on VeraCrypt 1.23 for Windows but most of it applies to VeraCrypt for Linux and Mac Os X as well.
VeraCrypt installation
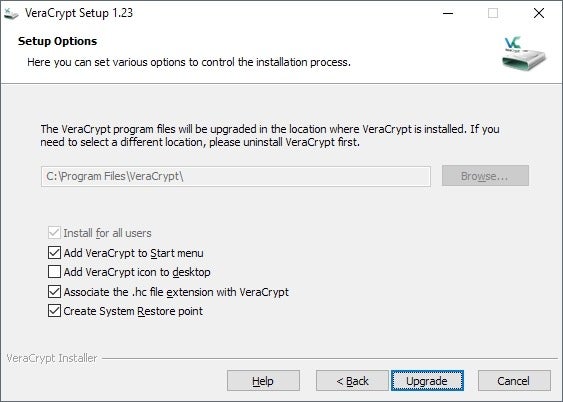
VeraCrypt is offered as a portable version and installer. You can download and extract the portable VeraCrypt archive and run it right away. The installer provides a few extra options such as adding an icon to the desktop or Start Menu, or associating the file extensions .hc with VeraCrypt.
The program creates a System Restore Point during installation and will install its drivers on the system. Note that it requires elevation because of that.
Using VeraCrypt
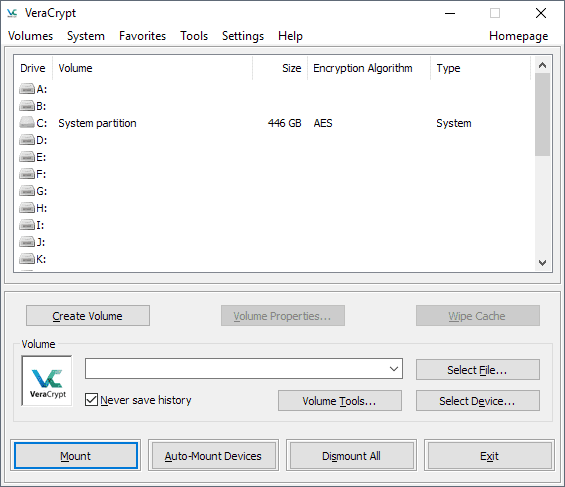
VeraCrypt's main interface looks almost like a copy of the classic TrueCrypt interface. The program lists available drive letters and mounted volumes at the top, and options to create, mount and dismount volumes in the lower half.
The menu bar links to additional tools, options and settings that new users may want to explore prior to creating a new container or encrypting a hard drive partition.
Interface options
- Create Volume -- starts a wizard to create a new container or encrypt a partition.
- Select -- The select options let you select an encrypted file (container) or hard drive partition for mounting.
- Mount options -- Select to mount the file or partition, dismount all, or configure auto-mount.
VeraCrypt Preparations
The very first thing you may want to do is go through all settings and some other steps to make sure everything is set up correctly.
Preferences
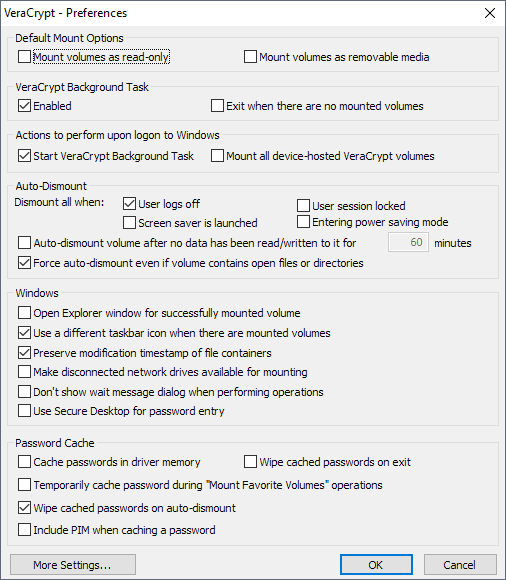
Select Settings > Preferences to open the general preferences. The developers squeezed a lot of settings on that single page and there is even a "more settings" button at the bottom that links to other Settings windows.
- Default mount options -- select to mount volumes as read-only or removable media. Read only prohibits writes to the drive and removable media defines certain parameters for the drive.
- Background Task and Startup -- VeraCrypt is loaded automatically on Windows start and a background task is up and running when users sign into the operating system. You can disable that here, configure VeraCrypt to exit when there are no mounted volumes or force the software to mount all device hosted VeraCrypt volumes automatically.
- Auto-Dismount -- Configure scenarios that dismount all mounted volumes automatically. VeraCrypt does so when users log off by default but you can enable the dismounting on lock, screen saver, power saving mode, or when no data is read or written for a set period.
- Windows-specific -- Gives you options to open Explorer automatically on mount, to use Secure Desktop for password entries for improved security, and to disable the wait message dialog during operations.
- Password Cache -- Define the use of the password cache and related options. Options include forcing VeraCrypt to wipe the cached password on exit (VeraCrypt does to automatically on dismount), or cache passwords in the driver's memory.
Here is a quick overview of other settings pages in VeraCrypt:
- Settings > Language -- change the interface language.
- Settings > Hot Keys -- configure system-wide hot keys to run certain operations such as dismounting all or wiping the cache.
- Settings > System Encryption -- Options that apply when you encrypt the system drive e.g. to skip the pre-boot authentication prompt by pressing the Esc-key.
- Settings > System Favorite Volumes -- Add volumes to the favorites.
- Settings > Performance and Driver Options -- Find out if AES hardware acceleration is supported, allow certain performance or driver related tasks such as TRIM or Defrag.
- Settings > Default keyfiles -- If you use keyfiles to authenticate (more about that later), you may add keyfiles to the list of default files.
Benchmark
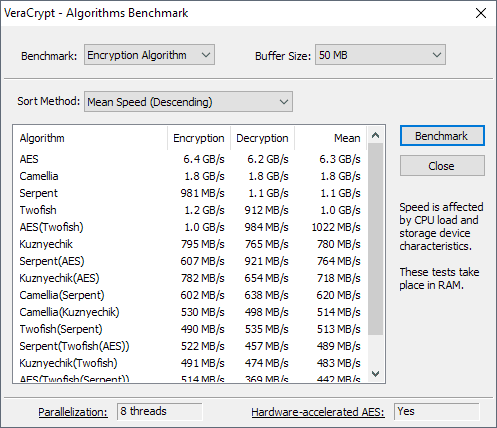
VeraCrypt includes a tool to benchmark all supported encryption algorithms. That's useful as it highlights which algorithms offer the best performance.
While you may select any supported encryption algorithm when you create new containers or encrypt volumes on the system, it is often best when you select a fast algorithm as it will speed up operations significantly.
Note: It is recommended that you create a backup of important data on the device before you use VeraCrypt to encrypt it.
Using VeraCrypt
VeraCrypt can be used to create encrypted containers -- single files that are stored on a drive that does not need to be encrypted -- or to encrypt an entire volume.
Volumes are divided into system volumes and non-system volumes. VeraCrypt supports both and can be used to keep all files as they are on a volume when you run the encrypt command.
- Container -- Single file that can have any size (file system limitations and volume limitations apply).
- System Volume -- The partition the operating system is installed on.
- Non-System Volume -- All other partitions.
The encryption process begins with a click on the "create volume" button. VeraCrypt displays the three available options on the first page and it is up to you to select one of the available options.
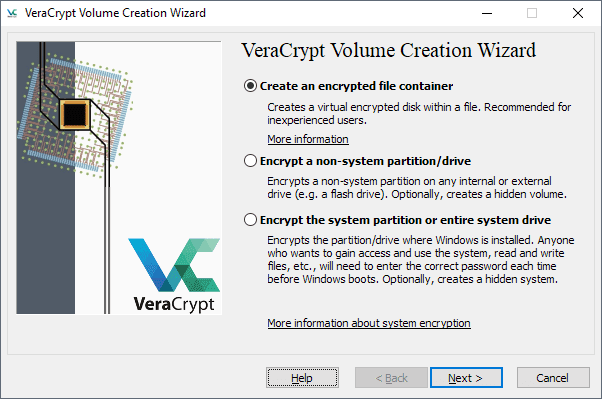
If you want to make sure that no one can access the computer or the data on it, you may want to select encrypt the system partition or entire system drive.
VeraCrypt displays an authentication prompt on boot then to decrypt the drive and boot the operating system. Anyone who cannot provide the password can't boot into the operating system.
The process is nearly identical for all three options. The core difference between creating a container and encrypting a partition is that you select a file when you select the former and a partition when you select the two other options.
- Standard or hidden volume -- You can create normal volumes or hidden volumes. Hidden volumes are created within standard volumes. If someone forces you to unlock the drive, only the standard volume is unlocked.
- Volume location -- Select a file (it gets created) or a partition that you want to encrypt.
- Encryption options -- Select an encryption and hash algorithm. You can run the benchmark from the page if you have not done so already.
- Volume Size -- Only available if you select the container option.
- Volume Password -- The master password that is used to encrypt the drive. You can use keyfiles and PIM as well. Keyfiles are files that need to be present to decrypt the drive and PIM. PIM stands for Personal Iterations Multiplier, it is a number that you need to supply when mounting volumes when you set it during setup.
- Volume Format -- Select the file system and cluster size. You are asked to move the mouse to create a random pool. Only available for some decryption operations.
There are two things that you may want to do after creating a new encrypted volume:
- Select Tools > Backup Volume Header to back up the volume header; useful if the volume gets corrupted.
- System > Create Rescue Disk to burn it to DVD or to a USB Flash Drive. Again, useful only if the system won't boot anymore or if the VeraCrypt boot manager has been overwritten or is corrupt.
You can mount containers or volumes at any time. Just use "select file" or "select" device" in the main interface, pick the desired target, and fill out the password (and other required things) to mount it as a new volume on the computer system.
Resources
VeraCrypt FAQ
Why was TrueCrypt development abandoned?
The (anonymous) developers of TrueCrypt never revealed why they abandoned the program. They did claim that the software was not safe to use, however.
Is VeraCrypt safe to use then?
TrueCrypt's code was audited and VeraCrypt fixed the security issues found by researchers during the audit. The developers of VeraCrypt implemented additional safeguards and improvements in the program, for instance by increasing the number of iterations significantly to make brute force attacks more difficult.
What are the main differences between VeraCrypt and TrueCrypt?
VeraCrypt uses its own storage format but supports the mounting and converting of TrueCrypt format volumes and containers.
Other major differences are that VeraCrypt includes fixes for vulnerabilities found in the TrueCrypt audit, that VeraCrypt supports PIM functionality, that it supports encryption of GPT system partitions, and that VeraCrypt system volumes don't need to be decrypted anymore during Windows 10 updates.
Which algorithms does VeraCrypt support?
VeraCrypt 1.23 supports the following algorithms:
- AES
- Camellia
- Kuznyechik
- Serpent
- Twofish
Combinations of cascaded algorithms are available as well:
- AES-Twofish
- AES-Twofish-Serpent
- Camellia–Kuznyechik
- Camellia–Serpent
- Kuznyechik–AES
- Kuznyechik–Serpent–Camellia
- Kuznyechik–Twofish
- Serpent–AES
- Serpent–Twofish–AES
- Twofish–Serpent
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments