Detect and Mitigate Intel AMT vulnerability
A recently disclosed vulnerability in Intel products using Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability gives attackers remote access to the manageability features supported by these products.
First the good news: the vulnerability does not affect (most) consumer PCs with Intel consumer firmware.
These technologies have been created by Intel for remote management of computer systems. Functionality may include monitoring, upgrading, repairing and maintaining compatible devices.
While you may use Intel's own advisory to find out if a computer system is vulnerable, it is easier to use the detection tool the company created and published for that instead.
You can download the tool from Intel's website, and may run it on all Windows versions starting with Windows 7. The program is portable, and it will tell you right away whether your system is vulnerable or not.
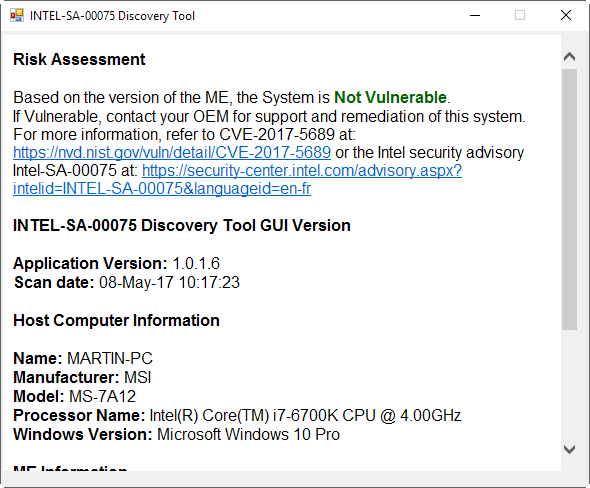
Note: Intel has published a guide to manually find out whether a system is vulnerable or not.
If the computer is not vulnerable, then you are done as there is nothing else to do. If the system is vulnerable however, you have one or two options depending on whether the manufacturer of the device has published an updated firmware already.
- First option is to check whether updated firmware has been released. If that is the case, update the firmware to plug the security vulnerability. You find the list of firmware updates on Intel's advisory page.
- If no firmware is available, you may use the third-party tool Disable Intel AMT, or one of Intel's suggested options described in the mitigation guide.
Disable Intel AMT is a basic batch file for Windows that renames the LMS.exe (Intel Local Management Service) binary so that it won't run anymore.
Intel's own solution requires multiple steps to complete. First, the unprovisioning of any provisioned system, then the disabling or deleting of the LMS service, and optionally configuring local manageability configuration restrictions.
Unconfiguring a system in CCM: ACUConfig.exe UnConfigure
Unconfiguring a system in ACM without RCS integration: ACUConfig.exe UnConfigure /AdminPassword <password> /Full
Unconfiguring a system with RCS integration: ACUConfig.exe UnConfigure /RCSaddress <RCSaddress> /Full
Intel published an unprovisioning tool which administrators may used if the above commands cannot be executed.
System administrators may also disable or remove LMS in the following way:
- Tap on the Windows-key, type cmd.exe, hold down the Shift-key and the Ctrl-key, and hit the Enter-key. This opens an elevated command prompt.
- To disable LMS: sc config LMS start= disabled
- To delete LMS: sc delete LMS
The vulnerability
If AMT is enabled, users may sign in locally or remotely. Intel uses HTTP Digest authentication for that, and anything that a user enters is computed to a hash and then authenticated by the interface.
The researchers discovered that the verification process that Intel implemented is flawed, as it accepts partial hashes or even an empty string. All an attacker requires therefore is knowledge of a working user account to sign in without knowing the correct password.
This article was first seen on ComTek's "TekBits" Technology News

- Log in to post comments